Who Are the Attackers?
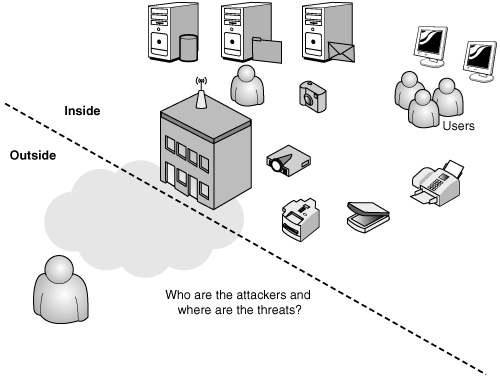
Who, from the perspective of an IT infrastructure, are internal attackers and external attackers? Internal attackers are commonly linked to disgruntled employees, contractors, or third-party users who, for whatever reason, have lost respect and integrity for the organization, including its IT infrastructure and its assets. External attackers are commonly linked to one of numerous attacker profiles or types. Figure 6.1 depicts a typical IT infrastructure and the domain between inside and outside threats.
Figure 6.1. Internal vs. external human threats to an IT infrastructure.
Which of the Two Attacker Types Is Potentially ... |
Get Inside Network Security Assessment: Guarding Your IT Infrastructure now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

