During this attack, we are going to craft an executable that will open a reverse connection between the target machine and our testing machine. To deliver this executable, we are going to place it on a USB device with a name that will pique the curiosity of the target. Once the USB is configured, leaving it in a public area in the target organization should produce the results we need.
The steps to perform our USB attack are as follows:
- From the main options list, we choose 1) Social Engineering Attacks:
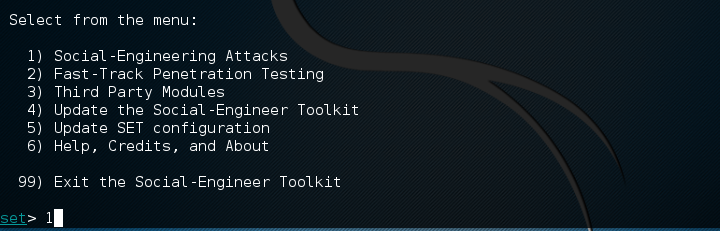
- To craft ...

