To perform DoS attacks using the exploit database, follow the given steps:
- Prior to using the exploit database to perform DoS testing, we will need to identify which DoS exploits are available. The total exploit database can be found online at http://www.exploit-db.com. Alternatively, a copy is locally stored in the Kali Linux filesystem. There is a files.csv file within the exploitdb directory that contains a catalog of all the contents. This file can be used to grep for keywords to help locate usable exploits:
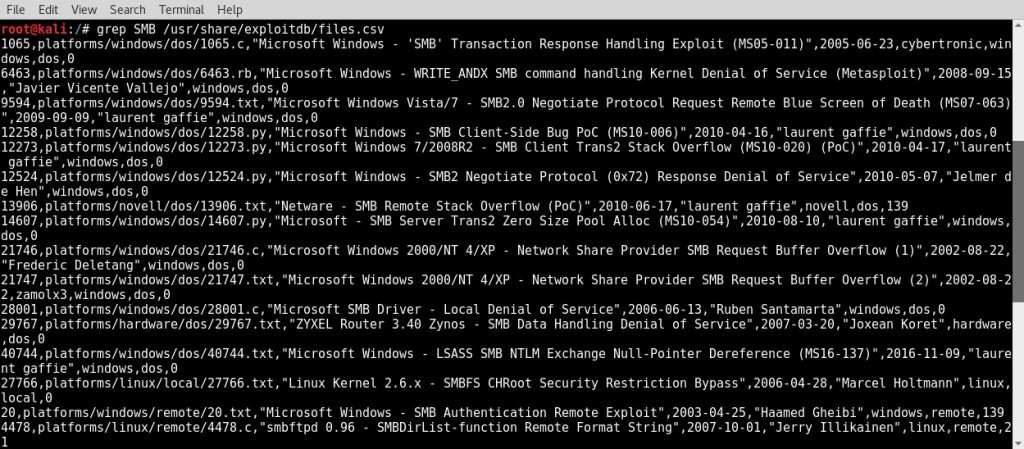
- In the example provided, the grep function was used to search the files.csv file for any exploit database contents ...

