For this exercise, it is preferable that we know the passwords for both users, although we only really need to know the attacker's password in a real-life scenario.
Configure the browser to use Burp Suite as a proxy and do the following:
- Log in as the user and go to account settings; click on the profile picture (top right-hand corner) and account settings:
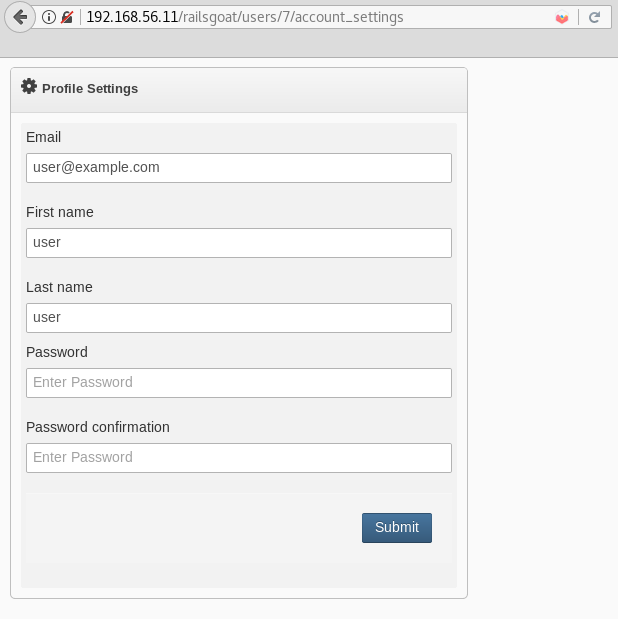
Notice that, in our example, the URL says users/7/account_settings. Could it be that that number 7 is a user ID?
- Log out and log in as the attacker.
- Go to account settings again and observe that the URL for the attacker settings has a different number.
- Enable request ...

