The use of Ghost Phisher can be seen as follows:
- We start it using the ghost-phisher command:
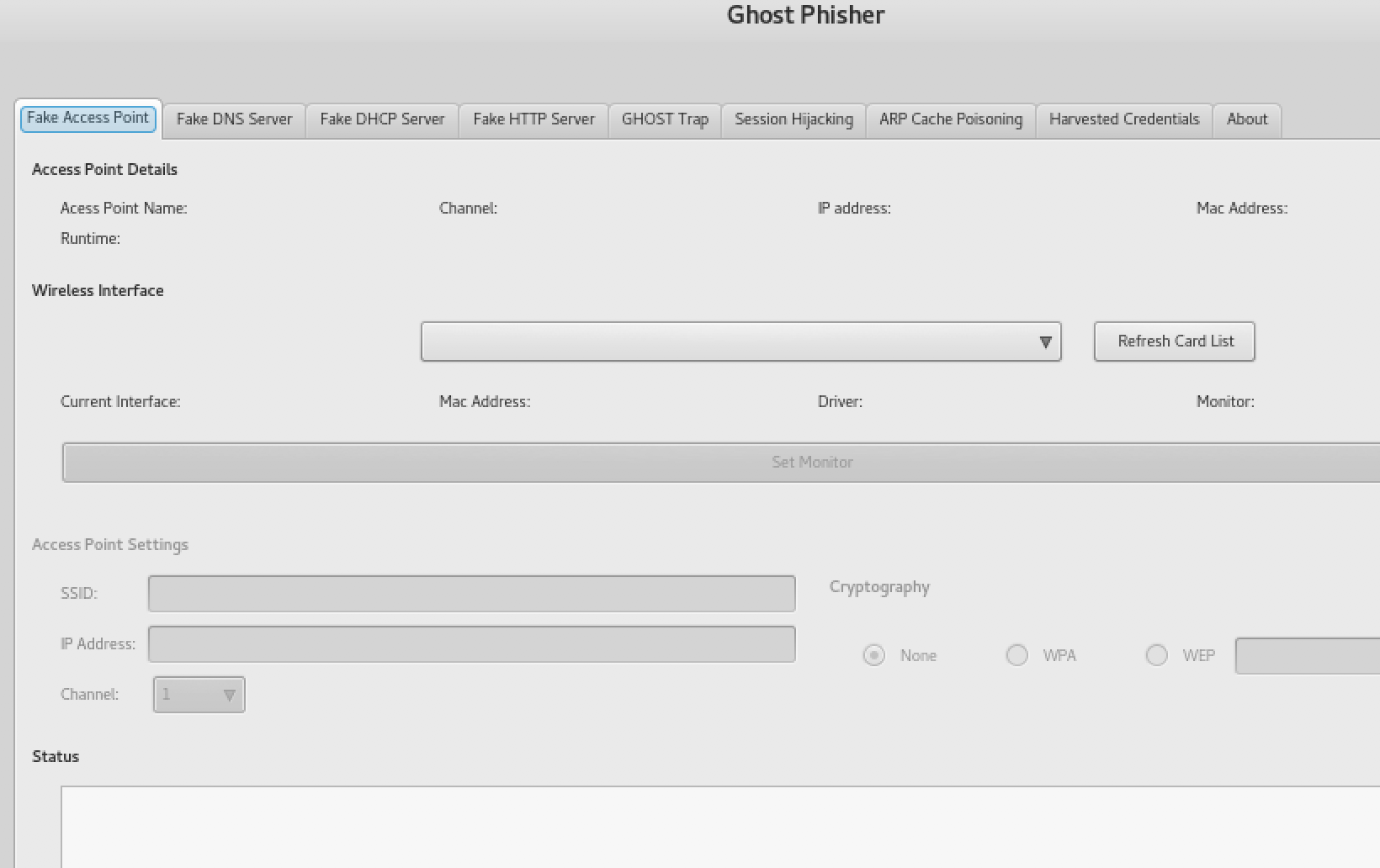
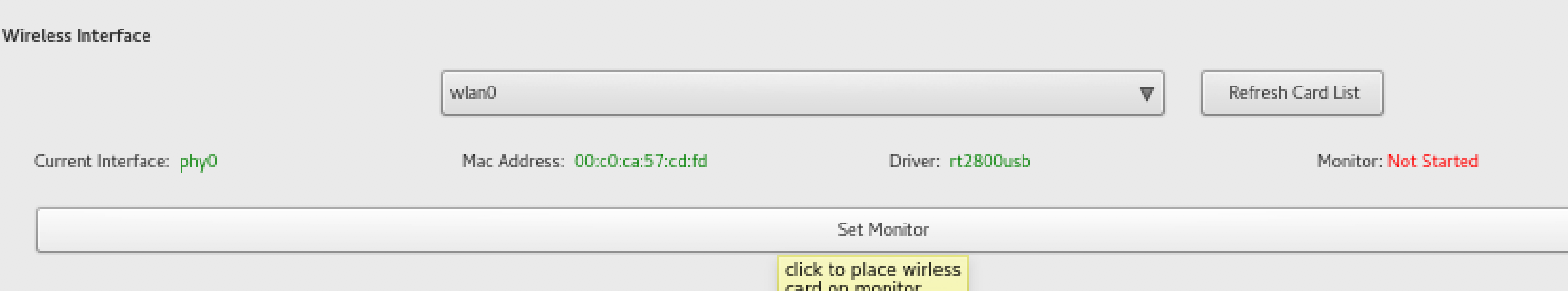
- Here, we choose our interface and click on Set Monitor:
- Now we enter the details of the access point we want to create:

- Then, we click on Start to create a new wireless network with that name.
- Then, we switch to a Fake DNS Server. Here, we need to mention the IP address the victim will be directed to whenever he/she opens any ...

