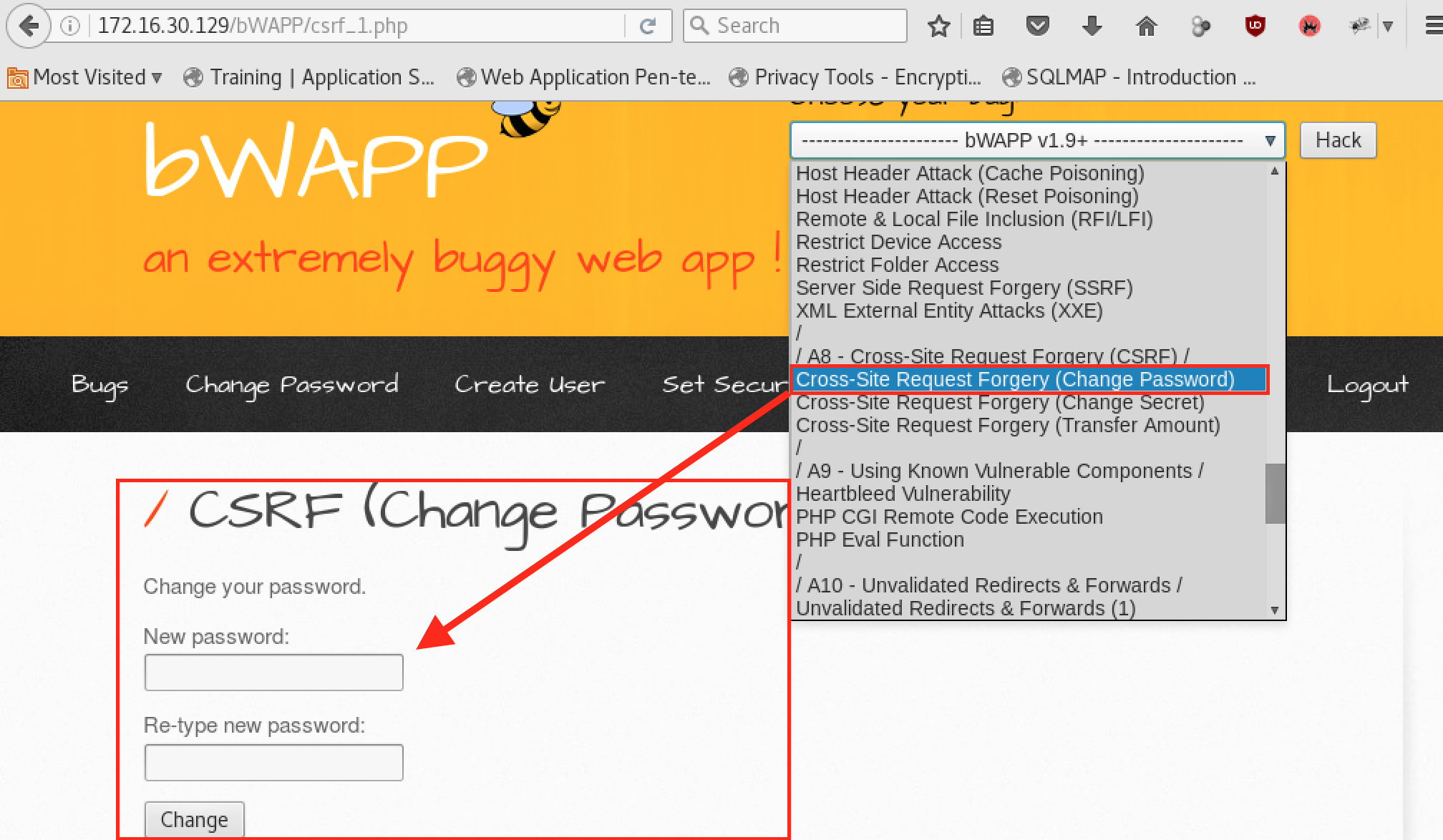
Conducting a CSRF attack, however, is not something typically conducted from these tools, but rather a browser and Notepad. If you find that CSRF might make sense in your testing, here is an example of how you might execute such an attack. For this exercise, we'll leverage the OWASP BWA VM and the Broken Web App (BeeBox) again and navigate to the appropriate page (as shown in the following screenshot):
Once we're in to the portal, we can go ahead and view the source of the portal (in Firefox this involves either using Ctrl + U or navigating to Tools | Web Developer | Page Source

