Advanced extended features of Metasploit
Throughout this chapter, we've covered a lot of post exploitation. Let's now cover some of the advanced exploitation features of Metasploit in this section.
Privilege escalation using Metasploit
During the course of a penetration test, we often run into situations where we have limited access and if we run commands such as hashdump, we might get the following error:

In such cases, if we try to get system privileges with the getsystem command, we get the following errors:
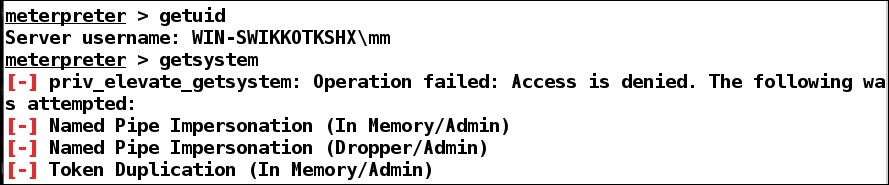
So, what shall we do in these cases? ...
Get Mastering Metasploit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

