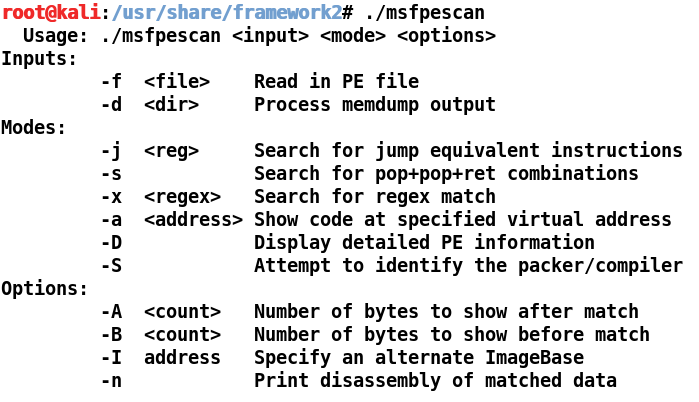
In the previous section, we found the DLL modules associated with the vulnerable application. Either we can use the Immunity Debugger to find the address of the JMP ESP instructions, which is a lengthy and time-consuming process, or we can use msfpescan to search the addresses for the JMP ESP instructions from a DLL file, which is a much faster process and eliminates manual searching.
Running msfpescan gives us the following output: