We will use a custom-made vulnerable application that uses unsafe functions. Let's try running the application from the command shell, as follows:
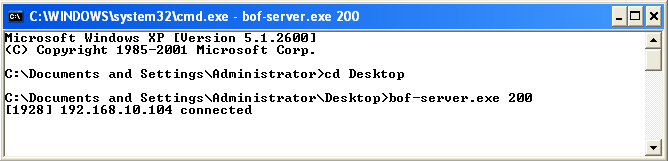
We can see that this is a small example application, which listens on TCP port 200. We will connect to this application via Telnet on port 200 and supply random data to it, as shown in the following screenshot:
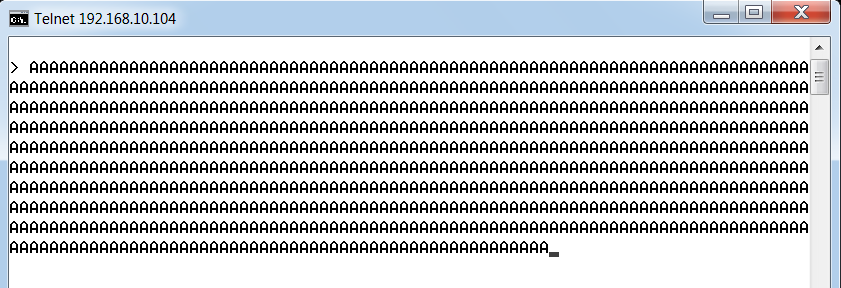
After we provide the data, we will see that the connection to the target is lost. This is because the application server has crashed. Let's see what it ...

