Chapter 14. Lightning’s Encrypted Message Transport
In this chapter we will review the Lightning Network’s encrypted message transport, sometimes referred to as the Brontide Protocol, which allows peers to establish end-to-end encrypted communication, authentication, and integrity checking.
Note
Part of this chapter includes some highly technical detail about the encryption protocol and encryption algorithms used in the Lightning encrypted transport. You may decide to skip that section if you are not interested in those details.
Encrypted Transport in the Lightning Protocol Suite
The transport component of the Lightning Network and its several components are shown in the leftmost part of the network connection layer in Figure 14-1.
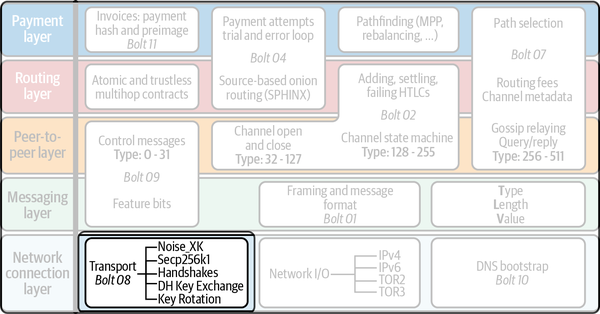
Figure 14-1. Encrypted message transport in the Lightning protocol suite
Introduction
Unlike the vanilla Bitcoin P2P network, every node in the Lightning Network is identified by a unique public key which serves as its identity. By default, this public key is used to end-to-end encrypt all communication within the network. Encryption by default at the lowest level of the protocol ensures that all messages are authenticated, are immune to man-in-the-middle (MITM) attacks and snooping by third parties, and ensures privacy at the fundamental transport level. In this chapter, we’ll learn about the encryption protocol used by the Lightning Network in ...
Get Mastering the Lightning Network now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

