19.6 A PRIVACY-AWARE LBAC SYSTEM
We now present a privacy-aware LBAC system that integrates the obfuscation techniques with the location-based access control system previously described.
19.6.1 LBAC Predicates Evaluation: 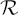 Eval Calculation
Eval Calculation
A major design issue for a privacy-aware LBAC architecture is related to the component in charge of evaluating LBAC predicates. Two choices are possible, which deeply affect how privacy is guaranteed.
- ACE evaluation: ACE, the component in charge of evaluating access control policies, asks users locations to the location middleware, without disclosing LBAC predicates. Locations are returned together with a relevance value.
- LM evaluation: ACE sends to LM an LBAC predicate for evaluation and receives a boolean answer and a relevance value.
Both choices are viable and well-suited for different set of requirements. On one hand, ACE evaluation enforces a clear separation between applications and location services because the location service infrastructure never deals with application-dependent location-based predicates. On the other hand, LM evaluation avoids the exchange of user locations, although obfuscated, with applications. This second choice is also more flexible in business terms. For instance, an ACE can subscribe to a location service for a specific set of location predicates and select different QoS according to different needs (e.g., different ...
Get Mobile Intelligence now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

