The Cyber Kill Chain framework was developed by Lockheed Martin to identify the actions required for adversaries to successfully exploit their targets:
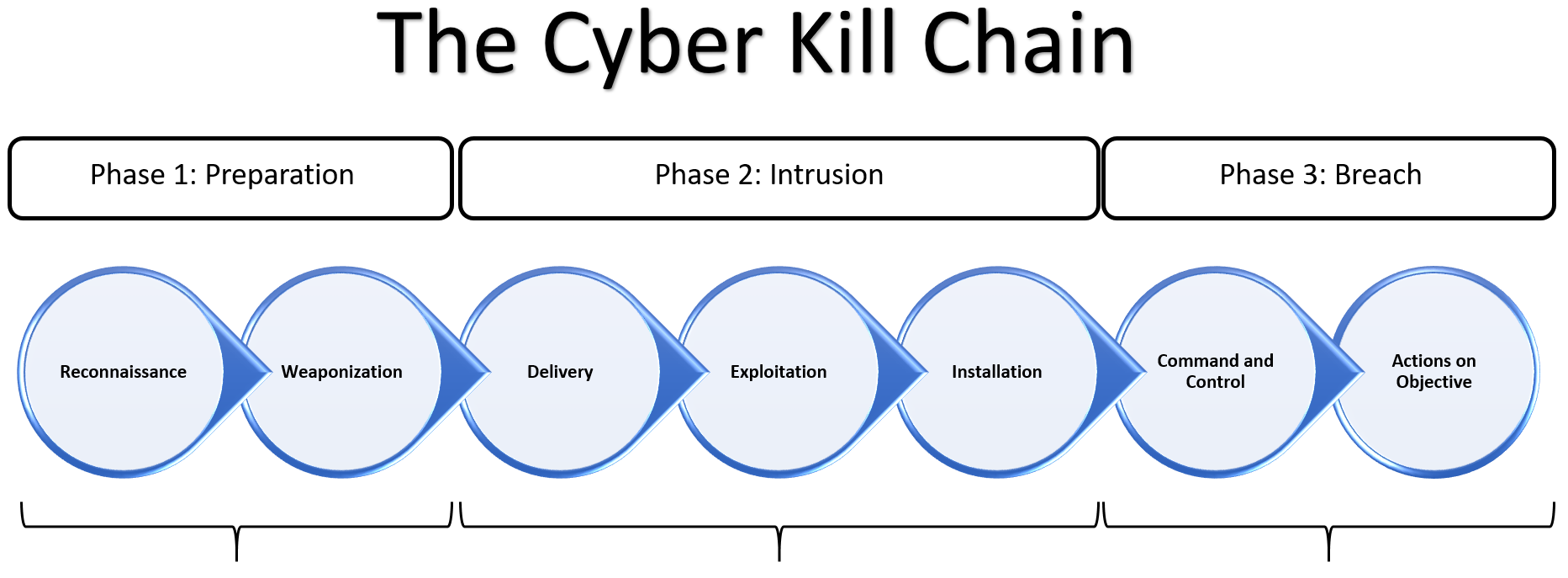
There are three phases that are comprised of seven steps in this framework:
- Phase 1: Preparation: The adversary is looking for the soft spots in your organization and figuring out a way to exploit a vulnerability:
- Reconnaissance
- Weaponization
- Phase 2: Intrusion: The adversary has found a vulnerability to exploit, a means to deliver it, and needs their target to take the bait so that it can begin taking control of targeted systems:
- Delivery
- Exploitation ...

