Understanding the Windows memory structure
The Windows Operating System (OS) memory structure has a number of sections that can be broken down into high level components. To understand how to write exploits and take advantages of poor programming practices, we first have to understand these sections. The following details break this information down into manageable chunks. The following figure provides a representative diagram of the Windows memory structure for an executable.
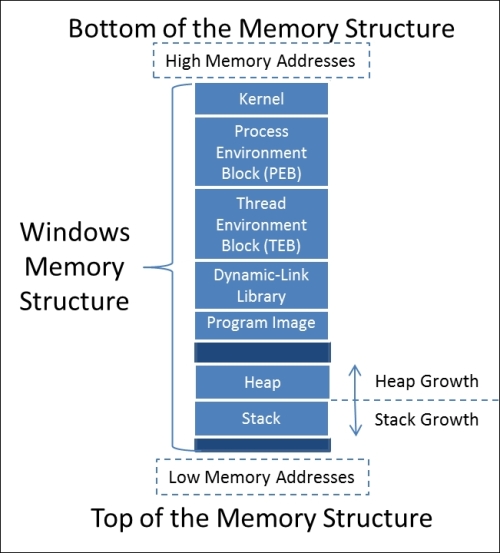
Now, each of these components is important, but the pieces we use with most exploit writing are the stack and the heap.
Understanding the stack and the heap
The stack is used ...
Get Python: Penetration Testing for Developers now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

