Activity monitoring – the detection of fraud involving mobile phones and proximity-based methods
Two major approaches of proximity-based methods are distance-based and density-based outlier detection algorithms.
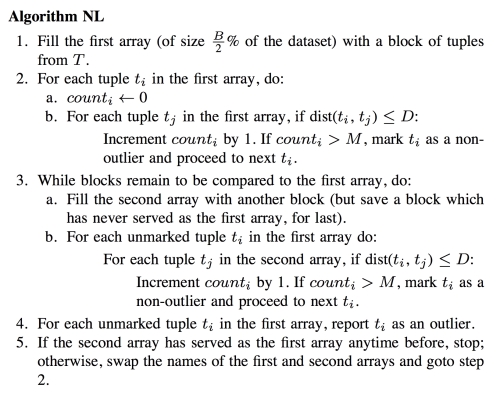
The NL algorithm
The summarized pseudocodes of the NL algorithm are as follows:
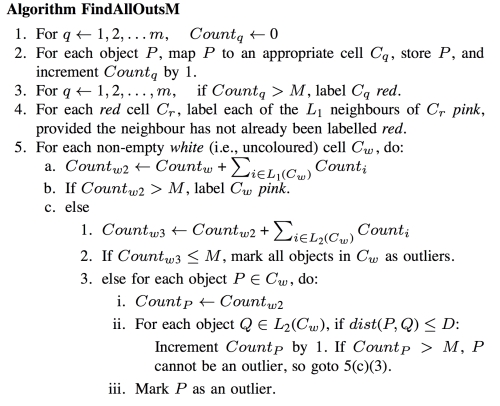
The FindAllOutsM algorithm
The following are the summarized pseudocode of the FindAllOutsM algorithm:
The FindAllOutsD algorithm
The summarized pseudocodes of the FindAllOutsD algorithm are as follows:
The distance-based algorithm
The summarized pseudocodes of the distance-based ...
Get R: Data Analysis and Visualization now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

