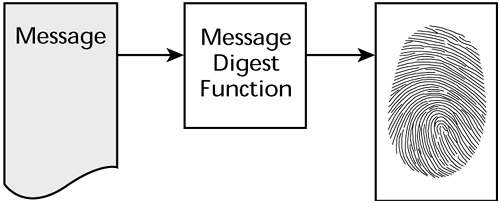
2.1. Message Digests
Message digest functions convert sequences of bits, possibly quite long, called messages, into fixed-length binary “fingerprints” or message digests of the original sequences. See Figure 2-1. A message digest function has two goals:
It should be computationally infeasible to find another message whose digest is the same as the digest of a given message.
It should be computationally infeasible to find two arbitrary messages whose digests are the same.
Figure 2-1. Message digest function
In the common case where an authentication method takes a large amount of computational effort and that effort is proportional to the number ...
Get Secure XML: The New Syntax for Signatures and Encryption now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

