10.4. Transforms and the Use of XPath
The raw data retrieved, based on the URI attribute in the Reference element or application context, is passed along through a pipeline of the Transforms, if any. The DigestMethod, which is effectively the last step in this pipeline, produces the DigestValue. See Figure 10-6. At each stage in the pipeline, the data can take one of two forms: a sequence of octets or an XPath node-set. Each Transform algorithm requires one of these forms as implicit input; the final DigestMethod requires an octet sequence for input.
Figure 10-6. The data pipeline
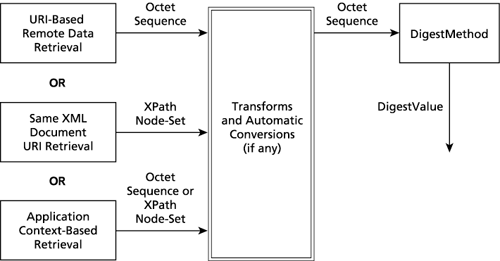
This process sounds straightforward, but some complexities arise. ...
Get Secure XML: The New Syntax for Signatures and Encryption now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

