Accessing a secured Hadoop cluster from an enterprise network
Typical deployment architecture of a secured Hadoop cluster in an enterprise context is shown in the following diagram:
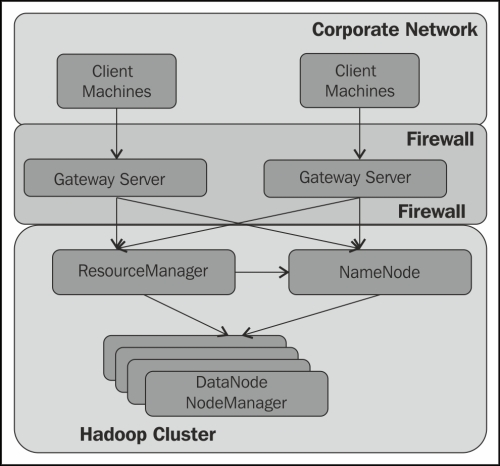
The Corporate Network is firewalled with the Hadoop cluster and connectivity is only provided through the EdgeNodes (also also known as Gateway Servers). The Gateway Server allows an entry point for external applications, tools, and users to the secured Hadoop cluster. It is deployed between the Hadoop cluster and the corporate network. As all users log in to this machine and the credentials for the user defined in this machine are used while accessing the Hadoop ...
Get Securing Hadoop now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

