Chapter 5. Security Misconfiguration
Security misconfiguration risk encompasses a broad category of configuration issues originated at any level of an application stack, including OS, network, application server, database, framework, or the application code itself.
Depending on the misconfiguration, the impact of vulnerability could range from an attacker identifying the platform and frameworks used to build the app to gaining a full control of the enterprise network and the application server.
As published in the HPE Cyber Risk Report 2016, Figure 5-1 shows the most commonly found vulnerabilities by analyzing more than 7,000 web applications. Incidentally, most of these vulnerabilities could be attributed to the security misconfiguration issues.
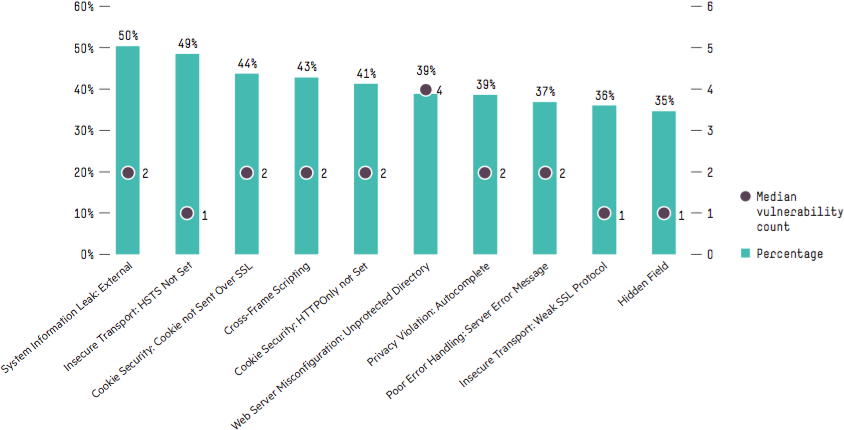
Figure 5-1. Top 10 most commonly occurring vulnerabilities from the data sample used for the HPE Cyber Risk Report 2016
This chapter covers related attack mechanics and ways to protect against them in Node applications.
Attack Mechanics
There are a variety of attack mechanics to exploit security misconfiguration, each affecting distinct attack surfaces. The subsections that follow present some examples.
Attacks from Browsers
An attacker can exploit the following security misconfigurations by using a browser or a browser-equivalent tool:
-
Any server configuration information leaked to the browser aids an attacker to build the security ...
Get Securing Node Applications now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

