Chapter 8
Forcing an Interception
Two business partners are at lunch. One jumps up and says, “I forgot to lock the safe! I have to go back to the office.” The other replies, “Sit down and stop worrying. We're both here.”
This joke makes light of the trust we place in others, even those we choose as business partners. The contents of an office safe are meant to be protected from threats, but attackers may actually be given as much or even the same access as the defenders. This chapter explores where, when, and how an attacker might gain this level of access.
Mapping the Infrastructure
Successful interception begins with a careful map of the defensive infrastructure. An attacker needs to know as much as possible about the defender to anticipate potential weak points and eventually take control of the asset. In doing so, the attacker increases his or her chances of success by focusing on potential vulnerabilities.
Consider a situation where a valuable package is being delivered from New York to London (see Figure 8.1). The asset is prepared in an office by one person, taken down an elevator, and given to someone else, who packages it for shipping and receiving. A third person picks up the package and takes it to a warehouse, where a fourth person sorts and routes it toward its destination.
Figure 8.1 Package route and transmission flow
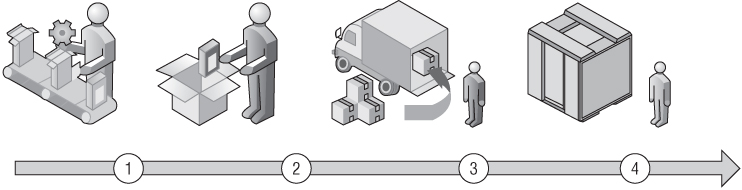
The package has not even left New York, and already ...
Get Securing the Virtual Environment: How to Defend the Enterprise Against Attack, Included DVD now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

