Examples of general threats and a control
Types of attack
Botnets
Bots are items of automated software running over the internet. A botnet is a group of computers controlled by a “bot herder.” Computer users can unwittingly add their computer to the group by visiting a rogue website. A botnet often comprises in excess of a million computers. (See “Zombie.”)
Man-in-the-middle attack
In this type of attack the attacker gets in between two parties who are communicating. See Figure A.2.
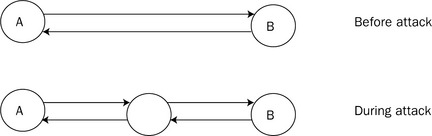
Figure A.2 How a man-in-the-middle attack works
Relay attack
In a “relay attack” (think relay race) information is relayed from one place to another ...
Get Security Risks in Social Media Technologies now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

