Chapter 1. Introduction to Serverless and Cloud Native
Serverless is an exciting new paradigm, and it’s taking the cloud-native world by storm. It promises dramatic value, ranging from extreme developer productivity through seamless elastic scaling to dramatic cost savings. On top of all of those, it boasts very real security benefits, too.
This short book explores this last point. It reviews how the serverless paradigm affects the security of an application, including the benefits it brings. More important, it helps you, the owner of the serverless application, understand what you should do to keep your serverless apps secure, and gives some practical tips on how to do so. Let’s begin in this first chapter with an overview of serverless and cloud native.
The Evolution of Cloud Native
To understand serverless, why it’s useful, and how it affects security, we need to first discuss the journey that led to its creation, and to do that, we need to take a short walk down memory lane and see how the cloud-native evolution unfolded.
An application in production is, in simple terms, made up of code that runs on servers, typically managing some state. This server and code duo interfaces with users and other systems, and typically reads and writes data to a database of some kind. Over time, the world of modern infrastructure has changed the nature of this underlying server, constantly striving for better resource utilization, lower management effort and greater agility.
Serverless is a controversial term. There’s ample debate about what serverless is, given that there are still, at the end of the day, servers running your code. We won’t explore this existential question in this book, but rather give one description of the journey to serverless, which should help clarify the security perspective in it.
From Hardware to Cloud
Not too long ago, the server on which your code ran was a physical machine that you had to buy and install on some rack. You provided it with data and power and did your best to keep it running. Even before cloud became a thing, most companies outsourced the physical hosting of these servers to datacenters and hired “remote hands” to help manage them, including securing physical access.
The next disruption to enter the scene was the virtual machine (VM). VMs allowed better resource utilization by running multiple virtual servers on one physical machine and sharing its use of memory and CPU. It also offered greater agility because you could provision and deprovision VMs without physically touching a server, increase resources by moving a VM to another machine, and so on.
After VMs went mainstream, there was little value in owning and operating the actual physical server, and so companies would rent those servers, instead. Eventually, newer vendors offered programmatic rental of such servers, unlocking greater agility by having a seemingly infinite pool of servers, along with cost savings resulting from renting servers by the hour, not month. These programmatic server farms are the basis for what we now call “the cloud.”
Containers
Enter containers. VMs are big and heavy, both in file size and startup times. In addition, multiple VMs running on the same physical machine share nothing, for instance loading the operating system (OS) into memory separately—even if it’s the exact same OS. Containers (e.g., Docker) are a lighter-weight form of virtualization, enabling resources already loaded into memory to be shared, which results in far better resource utilization.
A static container image (which holds the OS and components to be run) is built with the same sharing mindset. Container images are split into layers, allowing container runtimes (which run the images) to store only the bits for the same layer once, even if multiple images use it. This means fewer bytes to copy over the network or store in memory when running a new container image, offering greater agility, speed, and resource utilization.
Containers also have a profound impact on development practices, especially since Docker entered the scene. Although containers existed before, Docker introduced a simple model for building end-to-end container images, which bundle together the OS and app, manage layers, and offer easy tools for developers to run containers locally. It allowed developers to run their applications in a more production-like surrounding, boosting quality and productivity.
This evolution also triggered an important change in the organizational ownership of the OS. Physical and VMs, including those in the cloud, are typically managed by a separate IT team, who are also responsible for, among other things, keeping their OS updated and vulnerability free. With containers moving the OS into the build, developers need to take responsibility for keeping it secure and its dependencies patched. This is a significant change, and many organizations don’t handle it well yet.
Container Orchestration
So now we have these super-agile containers that you can slice and dice in many ways, efficiently move them around, and execute quickly and efficiently: hurray! Unfortunately, this flexibility introduces many moving parts, which need to be orchestrated—resulting in the next step of the evolution: container orchestration platforms (e.g., Kubernetes). These platforms help manage which containers go where, oversee security access permissions, launch systems, shut down systems, and many more tasks.
The most dominant container orchestration platform today is Kubernetes. Even though Kubernetes is meant to help manage many moving parts, running and operating Kubernetes itself is quite complicated in its own right and requires substantial expertise and time. This led to the creation of multiple “managed Kubernetes” platforms, which take this effort off your hands. The Big Three cloud platforms—Amazon Web Services (AWS), Microsoft Azure, and Google Cloud—offer general-purpose versions of these, whereas platforms like the Enterprise PKS (Pivotal Container Service) and RedHat OpenShift focus on enterprise needs such as on-premises installations, committed service for older versions, and more.
Serverless
And so, finally, we get to serverless!
At this point, we’ve traveled quite far from the physical machine that we used to run our applications on, but we’re still very much reliant on its CPU, memory, and other components. Even when orchestrating containers, we need to point to the (cloud) VMs they are on to run, and specify the hardware requirements for those. Amidst the many Kubernetes settings, we need to specify when to launch a new VM to grow our capacity. If we don’t manage it well, we either won’t scale to meet demand properly, or we’ll find ourselves paying for resources we’re not really using. Not great!
But it would be great if you didn’t need to manage that server capacity, right? If the managed cloud platform were to simply spin up a machine when required and then shut it down when it was no longer needed? If the OS was managed and patched by the cloud platform, therefore removing that burden from the Dev teams? That, in a nutshell, is the serverless promise. While clearly there are still servers running code, serverless really means server-management-less, pushing the effort of managing capacity and servers to the platform, as shown in Figure 1-1.
Serverless is primarily implemented through Function-as-a-Service (FaaS) platforms. Developers write small chunks of code, define when and how the function should be invoked (e.g., in response to an event or an HTTP trigger), wrap them as a function and push it onto the platform. When the triggering event occurs, the platform spins up a machine, deploys the function on it and executes it. Application owners pay purely for the resources used at a very granular level (per 100 ms of execution, for example), and don’t need to care whether the platform keeps servers up or takes them down (as long as request latency requirements are met).
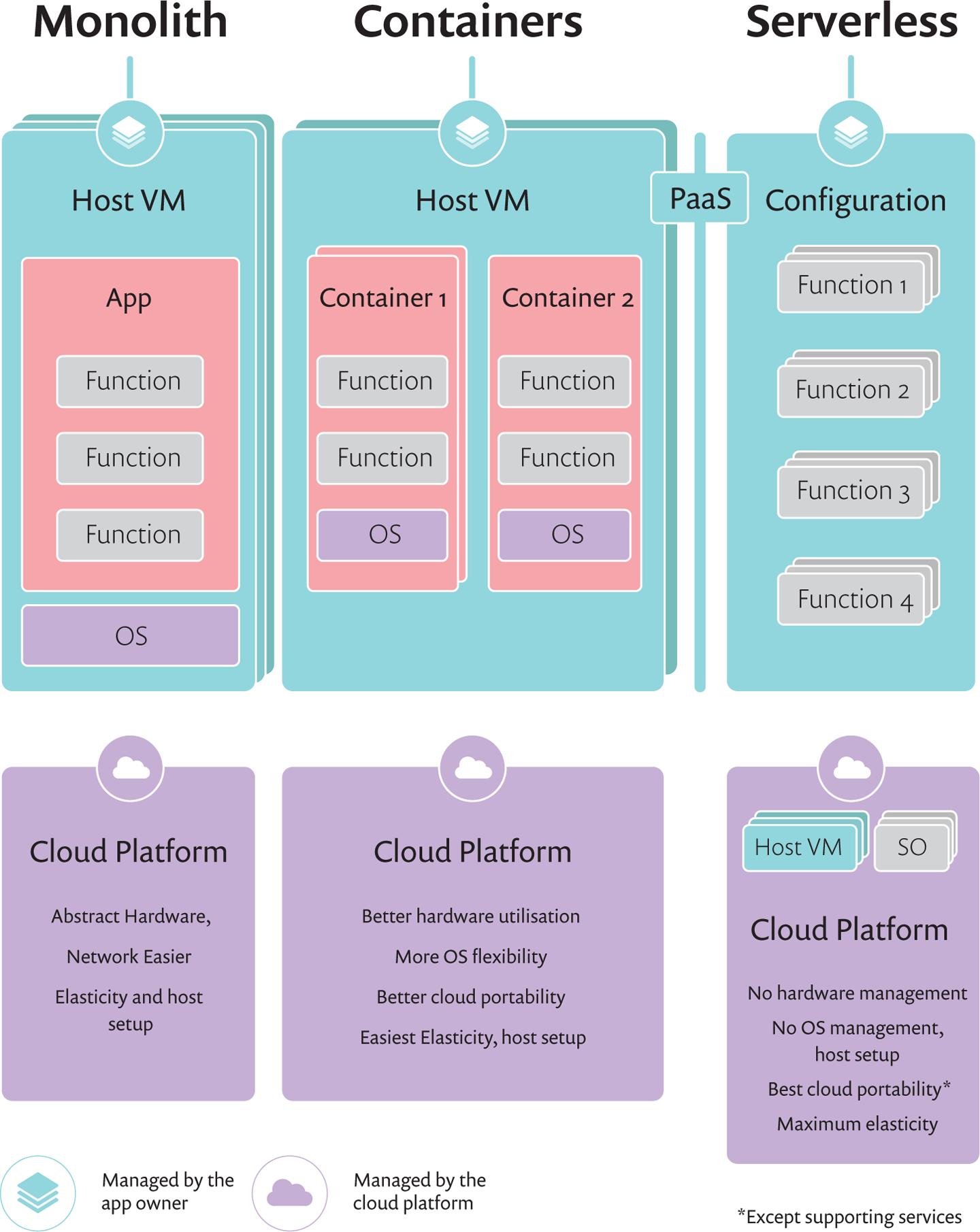
Figure 1-1. Monolith, containers, and serverless areas of responsibility and ownership characteristics
Despite the removal of infrastructure management, serverless still requires a fair bit of configuration and orchestration. Unlike containers, there’s no clear winner yet in how this orchestration is done, and much of it is still platform specific. As a result, every platform and approach carry some specific security considerations, ranging from default access to monitoring capabilities to the choice of VM reuse. In this book, we mostly stick to the serverless and FaaS concepts (and their security implications) and augment that with some concrete examples from different platforms.
Now that you understand what serverless is, in Chapter 2 we will review its security implications—for good and bad.
Get Serverless Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

