26.2. Model and rule structure
The most important aspect of the Common Policy model is that of additive permissions. This means that the privacy settings for a resource always start out with no permissions at all; the settings are then added with grants of permission by the user based on some form of stimulus – e.g., a user might find that another user wants to subscribe to her presence information via the watcher information [RFC3857] mechanism.
This is in contrast to a traditional blacklist model where everyone basically has access, except the blacklisted individuals. Blacklists have a major drawback in that simply changing one's identity – called "identity minting" – is enough to circumvent access controls.
Similarly to a whitelist model, additive permissions make the system much more privacy-safe and resistant to identity minting. Simply minting an identity is no longer enough to gain access; instead, a malicious user would actually need to get on another user's buddy list. Assuming identities are authentic and cannot be faked,[] getting on someone else's buddy list is hard to do; it would normally require an exchange of business cards or an earlier communication of one sort or another.
[] This is not an assumption that is easy to make – as the abundance of email spam has taught us.
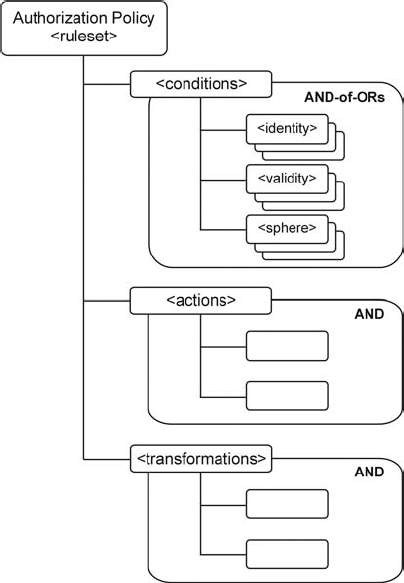
Figure 26.1. Common Policy data model.
Of course, applications benefit immensely from the ability ...
Get The IMS: IP Multimedia Concepts And Services, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

