CHAPTER 3: SAFETY UNDER THE PROTECTOR
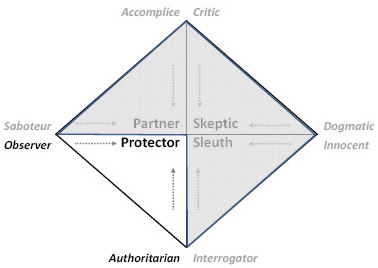
Figure 4: Protector archetype and shadows
When you turn the page in an IT audit or security textbook, words like attackers, hackers, cyber criminals pop up on almost every page. Budding IT auditors are trained to spot suspicious malicious insiders and guard against phishing, brute force, and other network attacks. The Protector archetype emerges when the Sleuth archetype identifies an area that needs securing (see Figure 4). Are our backups effective? Do we have a rollback plan for emergency program changes? Are controls in place for administrators or superusers? If not, what can be done? Management looks ...
Get Turning Heads and Changing Minds - Transcending IT Auditor Archetypes now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

