This is the kind of authentication with which we are more familiar: an HTML form that contains username and password fields and a submit button:
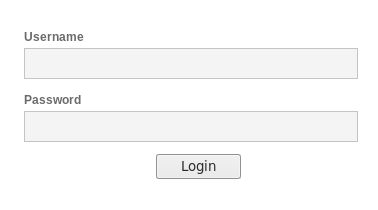
This authentication may vary from case to case, as its implementation is completely application dependent. Nevertheless, the most common approach follows these steps:
- The user fills in the authentication form and clicks on the Submit button. The client (web browser) then sends the request containing username and password to the server in cleartext, unless the client-side encryption is done by the application.
- The server receives the information and checks for the existence ...

