Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks have two major forms: eavesdropping and manipulation. Eavesdropping occurs when an attacker receives a data communication stream. This is not so much a direct attack as much as it is a leaking of information. An eavesdropper can record and analyze the data that he is listening to. A manipulation attack requires the attacker to not only have the ability to receive the victim’s data but then be able to retransmit the data after changing it, as shown in Figure 2-4.
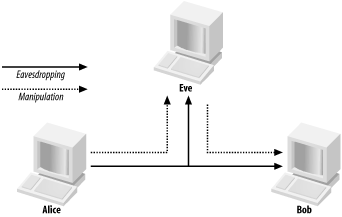
Figure 2-4. Eavesdropping versus manipulation
MITM attacks on a wired network generally require access to a network that the victim’s traffic transits. This can mean physical access to a wire to “tap” into the wire for interception. It can also mean being on the same LAN as the victim and forcing traffic to go through the attacker’s host. An attacker can force traffic through a malicious machine on a LAN by performing an ARP poisoning attack.
Get 802.11 Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

