OS Protection
In addition to securing the wireless connection itself, it is important to lock down the rest of the services running on the computer. Unneeded services should be disabled, and a firewall should be established to protect the host. It is also worthwhile to set up a static ARP address for the gateway to protect against man-in-the-middle attacks and automate the monitoring of logs.
Disable Unneeded Services
The System Preferences section titled Sharing controls what services will be run on the system. The Services tab, shown in Figure 7-4, controls what file-sharing services will be started on the system. Uncheck any of these you do not need to use. Remote Login is one service you might want to use; it provides a SSH login server to allow remote shell access.
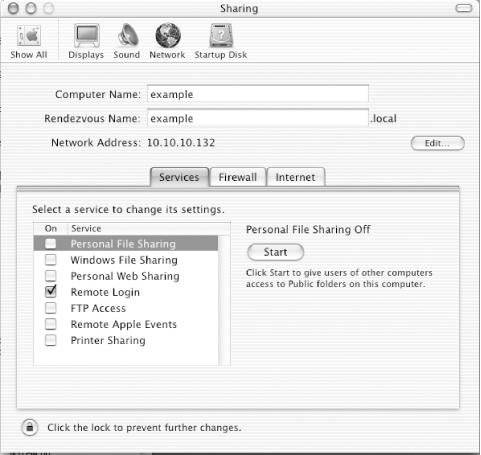
Figure 7-4. Services tab
Firewall Configuration
The Firewall tab of the Sharing configuration allows groups of ports to be filtered. Disable access to all services, unless you need to allow access. In the example shown in Figure 7-5, the firewall is off.
You can enable the limited firewalling configuration provided in this GUI setup program by pressing the Start button. If you want to use a more complicated set of filtering rules, it requires creating a script to run at system startup.
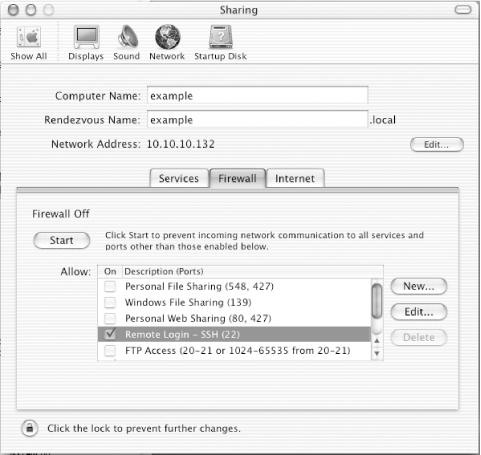
Figure 7-5. Firewall tab
If you don’t ...
Get 802.11 Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

