RISKS AND CONTROLS IN E-BUSINESS AND EDI (STUDY OBJECTIVE 8, continued)
Exhibit 8-19 in Chapter 8 summarized the risks and controls from the seller's perspective. That exhibit is presented here as Exhibit 9-20 to summarize risks and controls of electronic purchase transactions from the buyer's perspective, including security and confidentiality risks, processing integrity risks, and availability risks.
Exhibit 9-20 E-Business and EDI Risks and Controls
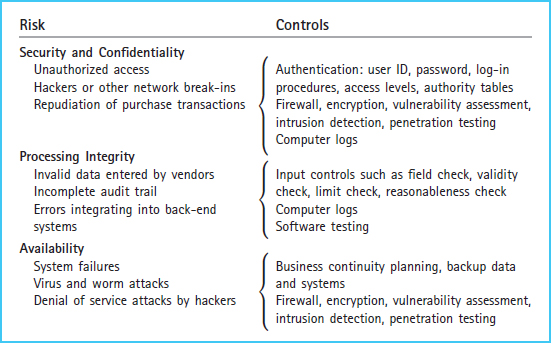
SECURITY AND CONFIDENTIALITY
When conducting purchase and payment transactions electronically, there must be an electronic link between buyer and seller IT systems. This electronic link might be in the form of private leased lines, third-party networks, or the Internet. No matter which type of electronic link is employed, the use of electronic links between buyer and seller exposes risks of unauthorized access and hacking or other network break-ins. Therefore, it is important that all users, including trading partners such as vendors, be authenticated when they access the system or records. The use of user IDs, passwords, and authority tables are intended to limit access to authorized users and to limit authorized users to only those files or records they must access to perform their assigned duties. Computer logs help management monitor user access and to discover unauthorized access and any resulting security breaches. Firewalls ...
Get Accounting Information Systems: The Processes and Controls, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

