The Mac AirPort is a tremendously popular access point. It looks like a slick, retro-futuristic prop from “War of the Worlds,” and it is very portable and rugged. While designed for use with the Mac platform, it works very well as a general purpose access point (and you don’t even need a Mac to configure it; see the next section). As I write this, the AirPort sells retail for about $299. What does that get you?
Direct Ethernet bridging
DHCP/NAT
56K dialup modem port
User-definable ESSID
Roaming support
MAC address filtering
WEP encryption
What doesn’t it get you? It has only one radio (actually, an embedded Orinoco Silver card) and no external antenna connector. But this isn’t much of a problem, because the internal Silver card itself has an external connector. See http://homepage.mac.com/hotapplepi/airport/or http://www.wwc.edu/~frohro/Airport/Airport.htmlfor examples of how to add your own antenna.
Out of the box, the AirPort will try to get a DHCP lease from the Ethernet and start serving NAT and DHCP on the wireless with no password. Yes, by simply plugging your new toy into your LAN, you have eliminated all of the hard work that went into setting up your firewall. Anyone within earshot now has unrestricted wireless access to the network you plugged it into!
While this could be handy as a default configuration (say, at a conference or other public access network), this probably isn’t what you want. To change the defaults, you’ll need configuration software.
If you
have a Mac handy, you are in luck. The
AirPort Admin utility that ships with
the AirPort is excellent (although only for Mac OS 9 or later). Apple has gone out of
their way to make the whole AirPort system easy to set up, even for
beginners. If you don’t own a Mac, you have a couple of
options. It turns out that the innards of the AirPort are virtually
identical to the Orinoco RG-1000 (previously, the Lucent Residential
Gateway). That means that the RG configuration utility for
Linux (called
cliproxy
) also works with the
AirPort. You can get a copy of Lucent’s
cliproxy utility at http://www.wavelan.com.
Jon Sevy has done extensive work with the AirPort and has released an open source Java client that configures the AirPort and the RG-1000. You can get a copy from http://edge.mcs.drexel.edu/GICL/people/sevy/airport/. He has also compiled a tremendous amount of information on the inner workings of the AirPort and has a lot of resources online at this site. Since his utility is open source and cross-platform (and works very well), we’ll use it in the following examples.
To use the Java Configurator app, you’ll need a copy of the Java Runtime Environment. Download it from http://java.sun.com/, if you don’t already have it. You can start the utility by running the following in Linux:
$ java -jar AirportBaseStationConfig.jar &
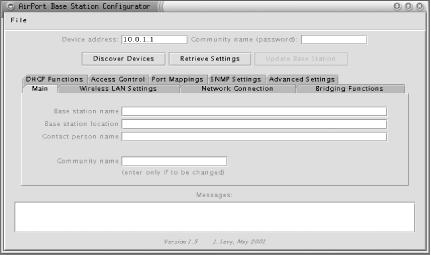
Or you can start the utility by double-clicking the AirportBaseStationConfig icon in Windows. Figure 4-1 shows an example of the configurator.
The AirPort can be configured over the Ethernet port or over the wireless. When the application window opens, you can click the Discover Devices button to auto-locate all of the APs on your network. When you find the IP address of the AP you want to configure, type it into the Device address field, and type the password into the Community name field. If you’re unsure about the IP address or the password, the AirPort ships with a default password of public and an IP address of 10.0.1.1 on the wireless interface (it picks up the wired IP address via DHCP; use Discover Devices to find it if you’re configuring it over the Ethernet). Once you’ve entered the correct information, click the Retrieve Settings button.
The very first thing you should change is the Community name on the first panel. Otherwise, anyone can reconfigure your AirPort by using the public default! While you’re there, you can set the name of the AirPort (which shows up in network scans) and also the location and contact information, if you like. These fields are entirely optional and have no effect on operations.
You should also choose a Network name, under the Wireless LAN Settings tab. This is also known as the ESSID, and it will identify your network to clients in range. If you’re running a “closed” network, it needs to be known ahead of time by any host attempting to connect, as described in the next section.
As stated earlier, the default AirPort configuration enables LAN access by default. If you’re using DSL or a cable modem, or if you are installing the AirPort on an existing Ethernet network, this is what you want to use. In the Java Configurator, take a look at the Network Connection tab and check the Connect to network through Ethernet port radio button.
From here, you can configure the IP address of the AirPort via DHCP, by entering the IP information manually, or by using PPPoE. You’ll probably want to use DHCP, unless your ISP requires a manual IP address or PPPoE.
There is also a radio button on the Network Connection tab marked Connect to network through modem. Use this option if your only network connection is via dialup. Yes, it’s very slow, but at least you’re wireless. Note that the dialup and Ethernet choices are exclusive and can’t be used at the same time.
When you check Connect to network through modem, the pane prompts you for phone number, modem init string, and other dialup-related fields. Make sure that Automatic dialing is checked, so it dials the phone when you start using the AirPort. Click on the Username/Password/Login Script button to enter your login information. On this screen, you can also define a custom login script, if you need to. The default script has worked fine for me with a couple of different ISPs.
Once the AirPort is configured for dialup, it will dial the phone and connect any time it senses Internet traffic on the wireless port. Just start using your wireless card as usual, and, after an initial delay (while it’s dialing the phone), you’re online.
By default, the AirPort acts as both a NAT server and a DHCP server for your wireless clients.[8] DHCP service is controlled by the DHCP Functions tab. To turn DHCP on, check the Provide DHCP address delivery to wireless hosts box. You can specify the range of IPs to issue; by default the AirPort hands out leases between 10.0.1.2 and 10.0.1.50. You can also set a lease time here. The lease time specifies the lifetime (in seconds) of an issued IP address. After this time expires, the client reconnects to the DHCP server and requests another lease. The default of 0 (or unlimited) is probably fine for most installations, but you may want to set it shorter if you have a large number of clients trying to connect to your AirPort.
If you don’t have another DHCP server on your network, the AirPort can provide service for your wired hosts as well. Check the Distribute addresses on Ethernet port, too box if you want this functionality.
Tip
Only check this box if you don’t have another DHCP server on your network! More than one DHCP server on the same subnet is a bad thing and will bring the wrath of the sysadmin down upon you. Watching two DHCP servers duke out who gets to serve leases may be fun in your spare time, but it can take down an entire network and leave you wondering where your job went. What were you doing connecting unauthorized gear to the company network, anyway?
If you have more than one AirPort on the same wired network, make sure that you enable DHCP to the wire on only one of them and, again, only if you don’t already have a DHCP server.
NAT is very handy if you don’t have many IP addresses to spare (and these days, few people do). It also gives your wireless clients some protection from the wired network, as it acts as an effective one-way firewall (see Chapter 3 for the full story of NAT and DHCP). In the Configurator, NAT is set up in the Bridging Functions tab. To enable NAT, click the Provide network address translation (NAT) radio button. You can either specify your own private address and netmask or leave the default (10.0.1.1 / 255.255.255.0).
A big disadvantage to running NAT on your wireless hosts is that they become less accessible to your wired hosts. While the wireless users can make connections to any machine on the wire, connecting back through a NAT is difficult (the AirPort provides some basic support for this by allowing for static port mappings, but this is far from convenient). For example, if you are running a Windows client on the wireless, the Network Neighborhood will show other wireless clients only and not any machines on the wire, since NAT effectively hides broadcast traffic (which the Windows SMB protocol relies on). If you already have a DHCP server on your wired network and are running private addresses, the NAT and DHCP functions of the AirPort are redundant and can simply get in the way.
Rather than duplicate effort and make life difficult, you can disable NAT and DHCP and enable bridging to the wire. Turn off DHCP under DHCP Functions (as we saw earlier), and check the Act as transparent bridge (no NAT) under the Bridging Functions tab. When the AirPort is operating in this mode, all traffic destined for your wireless clients that happens on the wire gets broadcast over wireless, and vice versa. This includes broadcast traffic (such as DHCP requests and SMB announcement traffic). Apart from wireless authentication, this makes your AirPort seem completely invisible to the rest of your network.
Once bridging is enabled, you may find it difficult to get the unit back into NAT mode. If it seems unresponsive to the Java Configurator (or Mac AirPort admin utility) while in bridging mode, there are a couple of ways to bring it back.
If you have a Mac, you can do a manual reset. Push the tiny button on the bottom of the AirPort with a paper clip for about two seconds. The green center light on top will change to amber. Connect the Ethernet port on your AirPort to your Mac and run the admin utility. The software should let you restore the AirPort to the default settings. You have five minutes to do this before the amber light turns green and reverts to bridged mode.
If you’re running Linux, you can easily bring the AirPort back online using Lucent’s cliproxy utility, without needing a hard reset. Run the following commands from a Linux machine (either on the wire or associated over the wireless):
$ cliproxy [ORiNOCO]> show accesspoints Searching... Hostname Eth Address IP Address Description ------------- -------------- ---------------- -------------------- NoCat 0030.42fa.cade 192.168.0.5 Base Station V3.64 [ORiNOCO]> configure remote 192.168.0.5 public Config loaded from 192.168.0.5 NoCat> configure terminal NoCat(config)> no service bridging NoCat(config)> service napt NoCat(config)> service dhcp-server NoCat(config)> done NoCat> write remote 192.168.0.5 public NoCat> exit
Of course, substitute your password for
publicand your IP address
for the previous sample. At this point, the AirPort should reboot
with NAT and DHCP enabled and bridging turned off.
If you’re running Windows and need to reset an AirPort in bridged mode, I suggest you make friends with a Mac or Linux user. You might be able to get things back to normal by doing a hard reset (holding down the reset button with a paper clip for 30 seconds while powering the unit up), but I’ve never been able to make that work. The previous two methods—using a Mac hard reset or the Linux cliproxy utility—have worked well for me in the past. I keep a copy of cliproxy handy for just this reason.
If you really want to lock down your network at the access point, you have the following tools at your disposal: WEP encryption, filtering on MAC address (the radio card’s serial number), and running a closed network. The three services are completely separate, so you don’t necessarily have to run MAC filtering anda closed network, for example. Combining all these features may not make your network completely safe from a determined miscreant, but it will discourage the vast majority of would-be network hijackers.
To set the WEP keys, click the Wireless LAN Settings tab and enter the keys in the fields provided. Also check Use encryption and uncheck Allow unencrypted data to require WEP on your network. Give a copy of this key to each of your wireless clients.
With MAC filtering enabled, the AirPort keeps an internal table of
MAC addresses that are permitted to use the AirPort. Click the
Access Control
tab and enter as many MAC
addresses as you like. Only radios using one of the MACs listed here
will be allowed to associate with the AirPort. The MAC address of a
radio card should be printed on the back of it (a MAC address
consists of six hex numbers of the form
12:34:56:ab:cd:ef).
A closed network makes the AirPort refuse connections from radios that don’t explicitly set the ESSID, i.e., clients with a blank ESSID or one set to ANY. To make your network closed, check the Closed network box under Wireless LAN Settings.
Remember that without encryption, all traffic is sent in the clear, so anyone within range could potentially read and reuse sensitive information (such as ESSIDs and valid MAC addresses). Even with WEP, every other legitimate user can see this traffic. If you need to restrict access to a user later, you’ll need to change the WEP key on every wireless client. But for small groups of trusted users, using these access control methods should discourage all but the most determined black hat without too much hassle.
Wireless roaming can be very handy if your network is arranged in a way that you can support it. In order for roaming to be possible, all your APs need to be from the same manufacturer, reside on the same physical wired subnet (i.e., on the same IP network, with no intervening routers), and have the same Network name (ESSID).
In the AirPort, roaming is automatically enabled if all of these are true. Make sure that all of your AirPorts have the exact same Network name under Wireless LAN Settings. If for some reason you want to disable roaming, just give each AirPort a different ESSID.
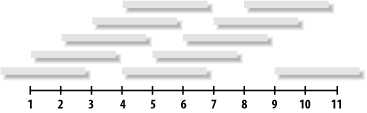
In the 802.11b specification (in the United States), the 2.4GHz spectrum is broken into 11 overlapping channels. Ideally, as you add access points to your network, you want to allow your coverage areas (or cells) to overlap slightly, so there are no gaps in coverage. Wherever possible, you should keep a spacing of at least 25MHz (or 5 channels) in adjacent cells, as shown in Figure 4-2. Otherwise, traffic on nearby APs can interfere, degrading performance.
Figure 4-2. Channels need to be separated by at least 25MHz to prevent overlap and possible interference
For example, you may use channels 1, 6, and 11 in an alternating pattern to provide complete coverage without any frequency overlap. Of course, everyone else using 802.11b is trying to do the same thing, and they will probably be using one of these channels. Especially in a crowded area, perfect 25MHz spacing may be impossible. If necessary, you may be able to get away with spacing as close as two or three channels, but don’t ever try to run two adjacent networks on the same channel (things may look fine at first, but will fall apart as the network load increases).
To figure out what channels your neighbors use, take a look at your signal strength meter and the other tools that your wireless card came with (the Orinoco card, for example, ships with an excellent Site Map utility). You might also check out NetStumbler, an excellent network discovery tool for MS Windows. You can get it online for free at http://www.netstumbler.com.
Get Building Wireless Community Networks now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.