Appendix C. Memory Tables
Chapter 1
Table 1-2 Security Terms
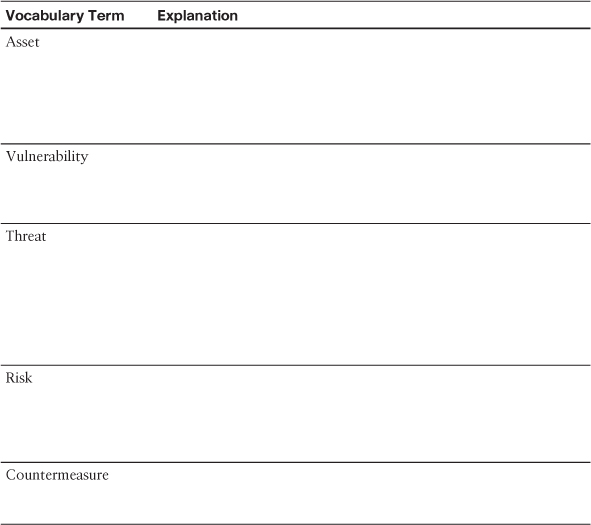
Table 1-5 Additional Attack Methods

Chapter 2
Table 2-3 The Who, What, and Why of Security Policies

Chapter 3
Table 3-2 Borderless Network Components

Chapter 4
Table 4-2 Components of a Threat Control and Mitigation Strategy
Table 4-4 Protecting the Data Plane
Chapter 5
Table 5-3 Properties ...
Get CCNA Security 640-554 Official Cert Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

