Packet filtering and firewalls
Firewalls are systems that regulate and monitor services passing between two networks, usually one that is trusted and the other untrusted. Extended access lists are the typical method of implementing firewalls with Cisco routers, since they are the preferred mechanism for filtering packets through the interfaces of two networks. In this section, we start with our simple example that controls access to a web server by packet filtering with an extended access list. We then continually expand the example, gradually including functionality and features to our small firewall to demonstrate how to build robust security policies.
A simple example of securing a web server
The first example of packet filtering demonstrates how to limit access to a web server to prevent the kinds of attacks described in Chapter 1. Before deciding what access lists are needed, it is often helpful to draw a diagram of network connectivity. Figure 3.4 shows the layout of the web server’s connectivity.
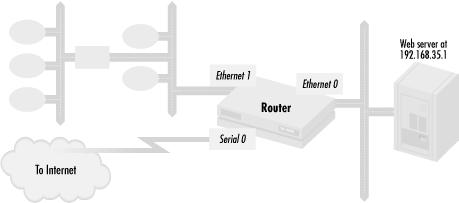
Figure 3-4. Restricting packets to a web server
We have a serial line to the Internet on the router interface serial 0. The web server lives on segment 192.168.35.0/24, with IP address 192.168.35.1 and uses the well-known web port, 80, and the well-known SSL port, 443, for delivering web services. Other hosts within the organization are connected to the router through interface Ethernet ...
Get Cisco IOS Access Lists now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

