Chapter 8. Designing and Implementing L2TPv2 and L2TPv3 Remote Access VPNs
In Chapter 2, “Designing and Deploying L2TPv3-Based Layer 2 VPNs (L2VPN),” you saw how Layer Two Tunneling Protocol version 3 (L2TPv3) can be used to transport a number of Layer 2 protocols in a site-to-site configuration. This chapter shows how L2TPv2 (RFC2661) and L2TPv3 (RFC3931) can be used to provide home workers, telecommuters, or “road warriors” with access to a corporate or other organization network.
Figure 8-1 depicts L2TP remote access VPNs.
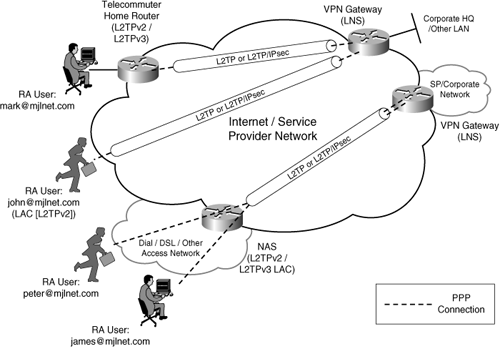
Figure 8-1. L2TP Remote Access VPNs
L2TP can be used to provide remote access in two different ways:
Voluntary/client-initiated ...
Get Comparing, Designing, and Deploying VPNs now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

