5.3 Implement appropriate security controls when performing account management
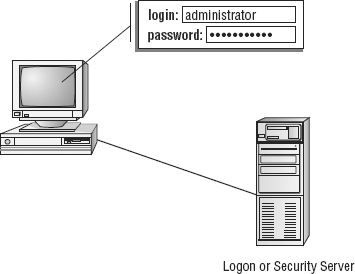
The combination of a username and a password is the most common form of authentication (see Figure 5.7). If the provided password matches the password stored in a system’s accounts database for the specified user, then that user is authenticated to the system. However, just because using a username and password is the most common form of authentication, that doesn’t mean it’s the most secure. On the contrary, it’s generally considered to be the least secure form of authentication.
FIGURE 5.7 A basic logon process employing a username and password
Numerous means to ...
Get CompTIA Security+™: Review Guide, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

