8.13 RC4
Designed in 1987 by Ronald Rivest of RSA Data Security, RC4 is a member of the suite of encipherment algorithms available in the Secure Socket Layer (Chapter 18). It provides security for wireless communications in Wired Equivalent Privacy (WEP), a protocol for wireless local area networks as defined in the IEEE 802.11b Standard.
RC4 generates a pseudorandom key stream consisting of a sequence of (8-bit) bytes. RC4 was a trade secret until 1994 and its name is still regarded as proprietary. RC4 has two components:
KSA – a key scheduling algorithm, which loads a key register with a permutation on integers 0 to 255; the key length varies from 40 to 128 bits;
PRGA – a pseudorandom number generator producing one 8-bit byte of key on each call of the generator.
8.13.1 The RC4 Algorithm
Key Scheduling Algorithm (KSA)
- Input
L bytes of key
k(1) = (k(0), …, k(L − 1)) with
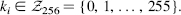
- Initialization
for i := 0 to 255 do
S[i] := i;
- Generation
j := 0
for i := 0 to 255 do
j := (j + S[i] + k(i(modulo L))) (modulo 256);
swap (S[j], S[j]);
TABLE 8.10 Key Register Cell Swapping in RC4
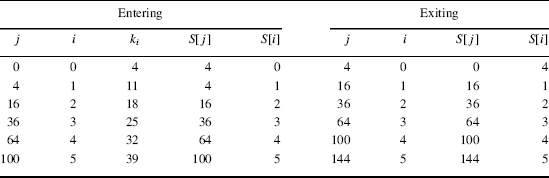
Example 8.9
If k = (4, 11, 18, 25, 32,…), the first six steps in KSA are given in Table 8.10. The contents of cells in the key register change; for example, the contents of S[4] undergo three changes during the KSA ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

