Appendix E. Proposed SwA Competency Mappings
When the model was developed, as part of our review process, several organizations mapped actual organizational positions to the competency model designations. This provided us with a checkpoint showing that our model designations were applicable to real organizations, and not just a theoretical exercise. These mappings are shown in Tables E.1 and E.2.
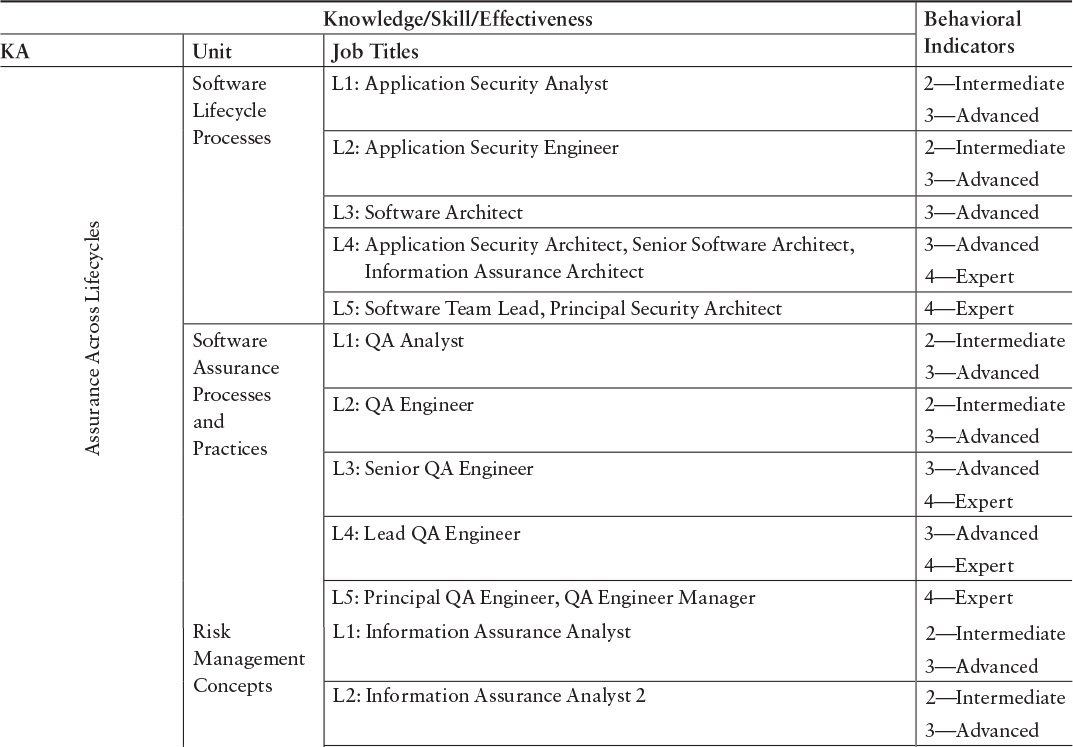
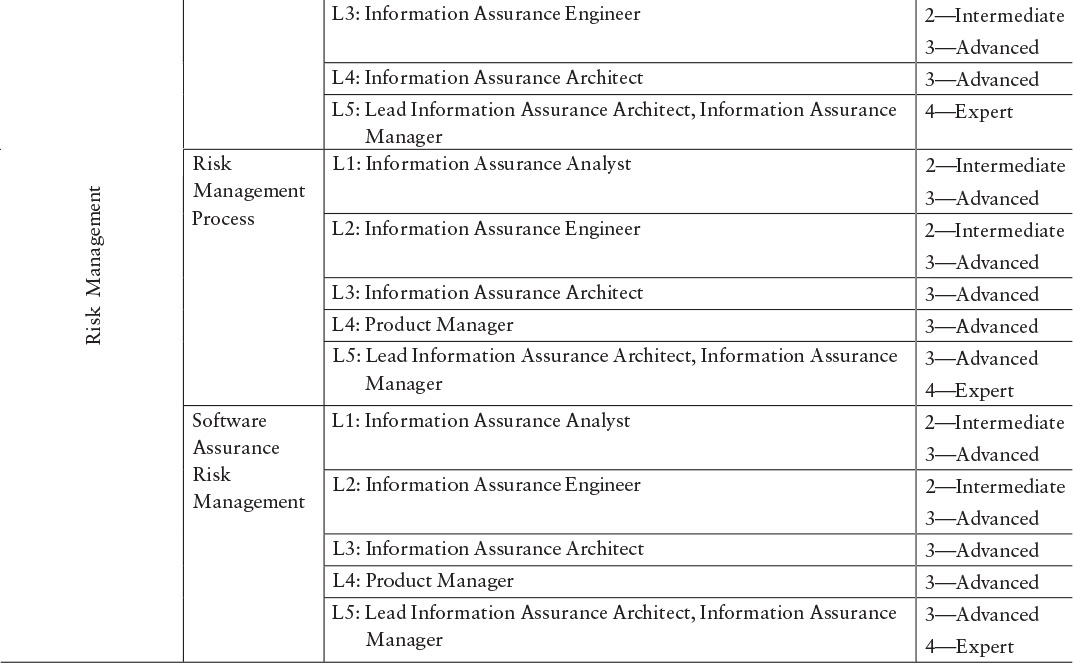
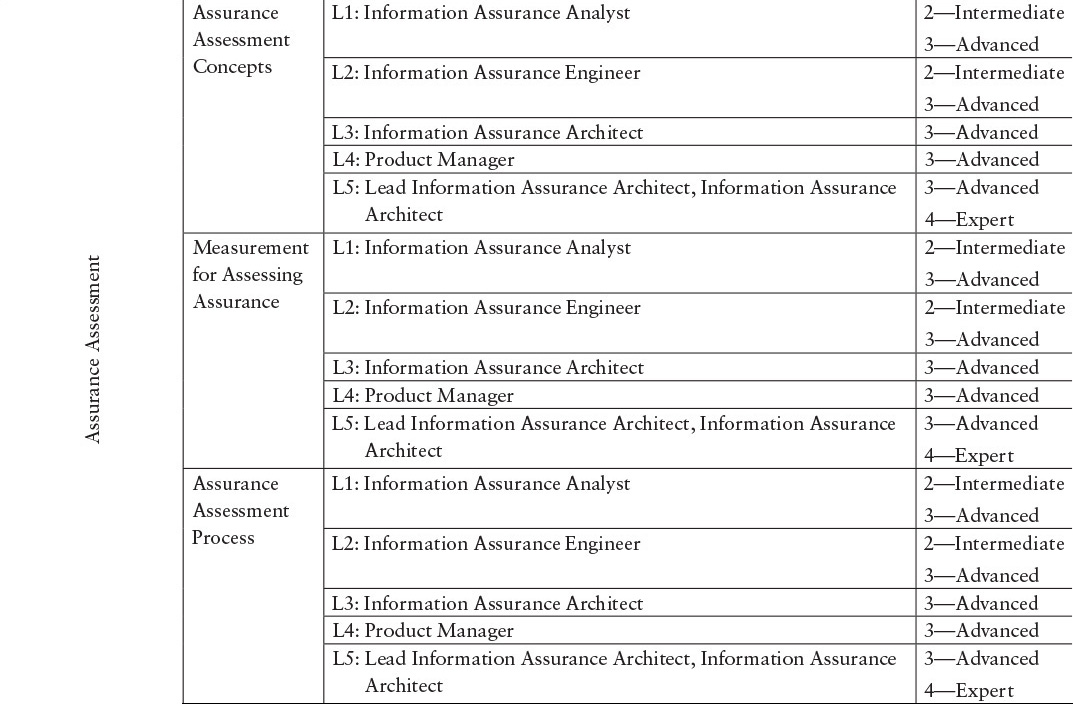
Table E.1 Proposed SwA Competency Mappings ...
Get Cyber Security Engineering: A Practical Approach for Systems and Software Assurance now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

