Chapter 4. Case Study: Firewall with a Perimeter Network
In the preceding chapter, you saw the mandatory configuration commands used to configure the zone-based policy firewall feature of Cisco IOS. In this chapter, we use those commands to develop a complete configuration of a firewall with a perimeter network shown in Figure 4-1. The policy rules used by this firewall are documented in Table 2-3 (Restrictive Policy of a Firewall with a Perimeter Network) of Chapter 2 “Typical Zone-Based Firewall Designs.”,
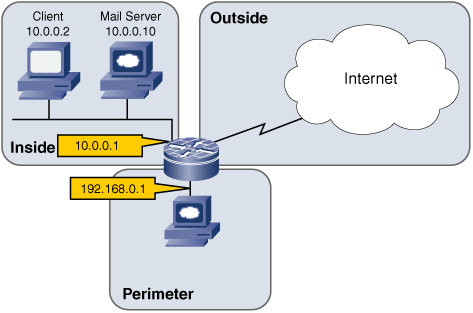
Figure 4-1. Firewall with a perimeter network ...
Get Deploying Zone-Based Firewalls now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

