▶ 8.6 Publishing Public Keys
We get the most benefit out of public-key cryptography if we publish and share public keys. This allows anyone to pick up a public key and encrypt a message to someone else. Attackers can’t use the public key to decrypt the message, at least not without breaking the system.
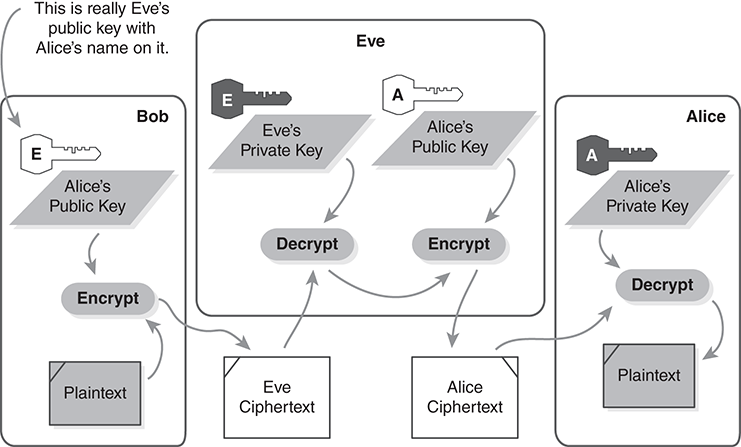
On the other hand, key cracking isn’t the only risk. There is also a trick in which an attacker actively intercepts all traffic. This is often called a man-in-the-middle attack. It is also known as the bucket brigade attack. FIGURE 8.26 provides a diagram of the action. Here is how it works:
Get Elementary Information Security, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

