Chapter 15. Security
Most enterprise applications are designed to serve a large number of clients, and users are not necessarily equal in terms of their access rights. An administrator might require hooks into the configuration of the system, whereas unknown guests may be allowed a read-only view of data.
It’s bad practice, however, to hardcode users’ access directly into your application’s logic. We shouldn’t have to rebuild an EJB each time a new employee comes into the company or an existing one is promoted to a new position with greater privileges.
If we group users into categories with defined roles, we can then allow or restrict access to the role itself, as illustrated in Figure 15-1.
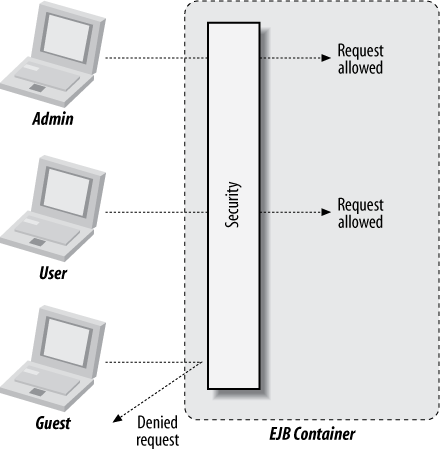
Figure 15-1. EJB security permitting access based upon the caller’s role
This technique is called role-based security. As we’ve seen before, embedding such rules within business logic tangles up concerns, so we’re best off enforcing these constraints at another level.
The Java EE and EJB specifications provide a core set of security services that application developers can integrate declaratively and programmatically. These include:
- Authentication
This is the process of validating the identity of a user who is trying to access a secured system. When authenticating, the application server verifies that the user actually exists in the system and has provided the correct credentials, such as a password. ...
Get Enterprise JavaBeans 3.1, 6th Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

