Chapter 5. Includes
As PHP projects grow, software design and organization play critical roles in the maintainability of the code. Although opinions concerning best practices are somewhat inconsistent (and a debate about the merits of object-oriented programming often ensues), almost every developer understands and appreciates the value in a modular design.
This chapter addresses security issues related to the use of includes—files that you include or require in a script to divide your application into separate logical units. I also highlight and correct some common misconceptions, particularly those concerning best practices.
Tip
References to include and require should also be assumed to include include_once and require_once.
Exposed Source Code
A major concern regarding includes is the exposure of source code. This concern is largely a result of the following common situation:
Includes use a .inc file extension.
Includes are stored within document root.
Apache has no idea what type of resource a .inc file is.
Apache has a
DefaultTypeoftext/plain.
This state results in your includes being accessible via URL. Worse, they are not parsed by PHP and instead are treated as plain text, resulting in your source code being displayed in the user’s browser (see Figure 5-1).
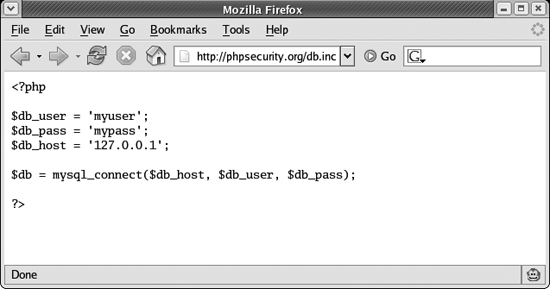 |
This problem is very easy to avoid. Simply organize your application so that ...
Get Essential PHP Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

