HTTP: The Definitive Guide
by David Gourley, Brian Totty, Marjorie Sayer, Anshu Aggarwal, Sailu Reddy
Symmetric-Key Cryptography
Let’s talk in more detail about how keys and ciphers work together. Many digital cipher algorithms are called symmetric-key ciphers, because they use the same key value for encoding as they do for decoding (e = d). Let’s just call the key k.
In a symmetric key cipher, both a sender and a receiver need to have the same shared secret key, k, to communicate. The sender uses the shared secret key to encrypt the message and sends the resulting ciphertext to the receiver. The receiver takes the ciphertext and applies the decrypting function, along with the same shared secret key, to recover the original plaintext (Figure 14-7).
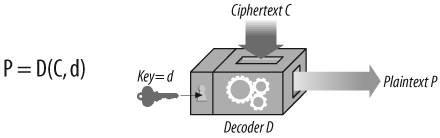
Figure 14-7. Symmetric-key cryptography algorithms use the same key for encoding and decoding
Some popular symmetric-key cipher algorithms are DES, Triple-DES, RC2, and RC4.
Key Length and Enumeration Attacks
It’s very important that secret keys stay secret. In most cases, the encoding and decoding algorithms are public knowledge, so the key is the only thing that’s secret!
A good cipher algorithm forces the enemy to try every single possible key value in the universe to crack the code. Trying all key values by brute force is called an enumeration attack . If there are only a few possible key values, a bad guy can go through all of them by brute force and eventually crack the code. But if there are a lot of possible key values, it might ...