Security Concepts
Everybody wants to have a secure network, but providing that security is often a very complex and difficult process due to the multiple levels that need to be examined. For example, it does not do much good if you provide very detailed filters and access privileges on a router, when the physical access is an unlocked door in a wiring closet at a remote location. Security must not be an afterthought; it must be designed literally from the ground up, from physical access to the network to filters that allow only certain types of traffic. When implementing security at any layer, design toward the security concepts that are displayed in Figure 6-1: integrity, availability, and confidentiality. These concepts will help to build the network’s circle of trust.
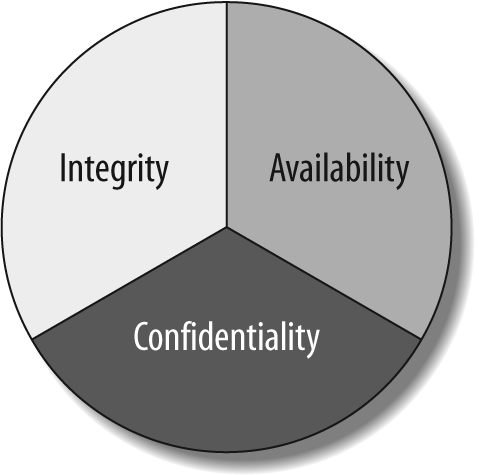
Figure 6-1. Security circle of trust
The first concept of security design is to ensure the integrity of the data. In other words, the data should not be altered in any way without purpose. This includes data that could be modified by unauthorized personnel, but does not exclude data manipulation by authorized personnel. Many network breaches are sourced from an “insider,” someone who either works or did work for the company. This could be a disgruntled employee who decides to wreak havoc on the network because he never received his new office stapler! Also, data integrity implies that the data is consistent across internal ...
Get JUNOS Enterprise Routing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

