Working with Certificates
Certificates are necessary part of securing messages. They make it possible to authenticate clients and services, they can be used for authorization, and they are used to protect messages with digital signatures and encryption. There are a few common scenarios that warrant the use of certificates for client credentials:
Certificates can be used to identify business partners. The service provider may issue the certificates to trusted partners, or they may collect the public keys of trusted partners for authorization. This scenario is shown in Figure 7-8.
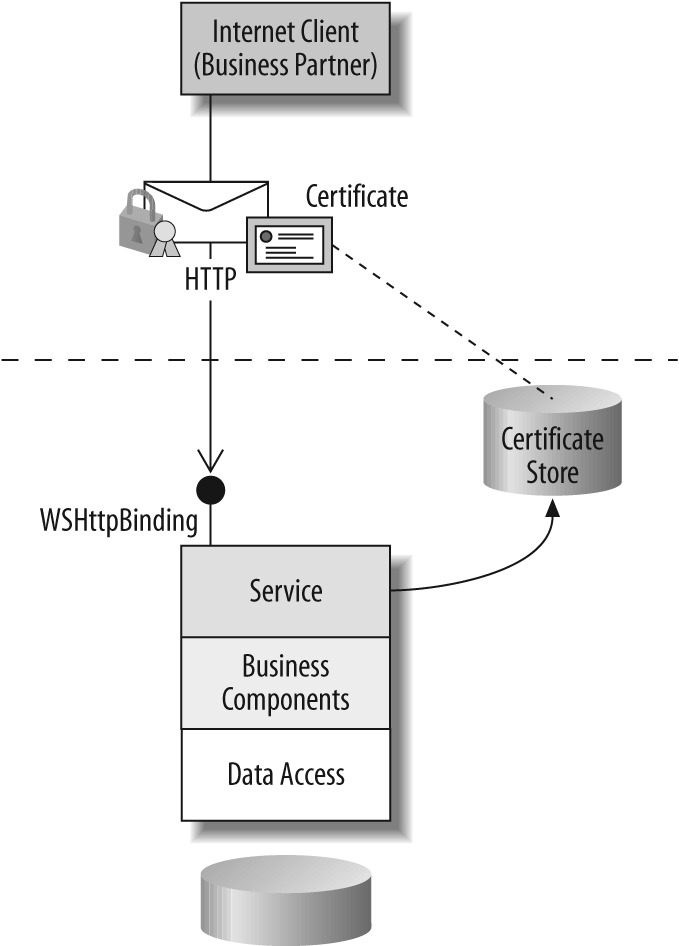
Figure 7-8. Business partner scenario
Certificates can be useful for authenticating across machine boundaries behind the firewall in a trusted subsystem scenario. In this case, the client may be an application as shown in Figure 7-9 or another service as opposed to an individual or business partner.
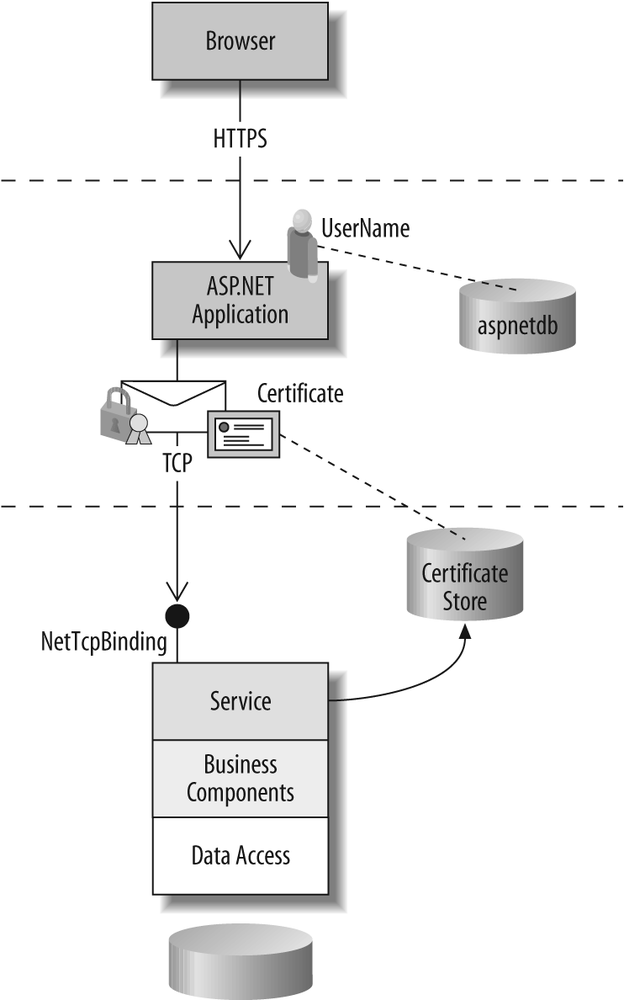
Figure 7-9. Trusted subsystem scenario
In this section, I’ll first explain some key terms and concepts related to certificates. After that I’ll describe scenarios for using certificates to protect messages and implement mutual authentication scenarios.
Understanding Certificates, Digital Signatures, and Encryption
Public Key Infrastructure (PKI) is a general term that refers to cryptography technologies and related network ...
Get Learning WCF now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

