Malicious mobile code (MMC) is any software program designed to move from computer to computer and network to network, in order to intentionally modify computer systems without the consent of the owner or operator. MMC includes viruses, Trojan horses, worms, script attacks, and rogue Internet code. The intentional part of the definition is important. Design flaws in the Microsoft Windows operating system are responsible for more data loss than all the malicious code put together, but Windows wasn’t intentionally designed to destroy your data and crash your system. And it certainly doesn’t sneak on your hard drive without permission to get there. MMC used to mean DOS computer viruses, Trojans, and worms. Today, you have to add all harmful programs created with scripting languages and empowered by Internet technologies: macro viruses, HTML, Java applets, ActiveX, VBScript, JavaScript, and instant messaging. There are even viruses that infect Windows help files. Today, simply scanning executable files and boot sectors isn’t enough.
There is a technological war going on. There are good guys and bad guys. Every second of every day, tens of thousands of pieces of MMC are trying to break into some place they shouldn’t be, delete data, and mess up the day of many fine people who are just trying to work. Mischievous hackers write malicious code and release it in to the unsuspecting world. People lose data and productive time as bugs are discovered and removed. Antivirus researchers and security experts take apart the latest creation to learn how to detect and remove it. The public is educated, security holes are closed, and software scanners are updated. But this does little to stop the next attack. The next one is a slight variation (called a variant ) from the older exploit or maybe even something completely different. In either case, the maliciousness occurs again with the same results. The defense steps most of us are taking are not enough.
It’s a real war. If the general public knew what was possible, they might not want to get on the Internet. There are automated malicious programs, bots, and scripts, all designed to fight it out with the good guys. They look for weaknesses in control and then automate the attack. So many new malicious programs are being developed that most of them don’t even interest the good guys. Only the ones that do something new invoke curiosity. Antivirus researchers have automated bots that scour the Internet, much like a search engine would, looking for MMC. It would be too time consuming for humans to do it. When found, the viruses, worms, and Trojans are fed into software tools that automate the process of disassembly, debugging, and identifying the catch. Some antivirus companies are cataloging 200-400 new malicious programs a month, with some vendors saying their products now catch over 54,000 different bugs.
Tip
A bot, short for robot, is a software program designed to dig through lots of data looking for predefined clues. Bots, also called agents, are used throughout the Internet. Most search engines use bots to “crawl” through the World Wide Web and bring back URL addresses.
Fortunately, we do have the good guys on our side and even most of the smart bad guys aren’t out to destroy your data. To date, even the biggest malicious code threats have only caused days of downtime. Now, multiplied by hundreds of thousands of machines, the aggregated time spent fixing the damage makes a pretty impressive figure. But for the most part, once the damage is fixed and the hole closed, business goes back to normal. Why should you care then? Because I’m sure you are like me and don’t like strangers poking around in your data.
MMC does cause real damage and real downtime. If you take the time to learn what the threats are and how to prevent them, you can save more time in the end. Just learning about what is possible prepares you to make better decisions and implement appropriate security. The only companies hurt by the 1992 Michelangelo virus panic were the ones who never scanned for it even after the warning alarm was sounded. Knowledge is power and job security.
Most malicious code programs can be categorized as a virus, Trojan, worm, or mixture. A rogue program may be written in assembly language, C++, Java, or in Visual Basic for Applications (VBA), but it still is classified as one of these major types. Unless, that is, the malicious program functions as two or more of these types.
- Virus
A virus is a malicious program that modifies other host files or boot areas to replicate (a few exceptions). In most cases the host object is modified to include a complete copy of the malicious code program. The subsequent running of the infected host file or boot area then infects other objects.
- Trojan
A Trojan, or Trojan horse, is a nonreplicating program masquerading as one type of program with its real intent hidden from the user. For example, a user downloads and runs a new, free version of his favorite multiplayer game from a web site. The game promises thrills and excitement. But its true intent is to install a Trojan routine that allows malicious hackers to take control of the user’s machine. A Trojan does not modify and infect other files.
- Worm
A worm is a sophisticated piece of replicating code that uses its own program coding to spread, with minimal user intervention. Worms typically use widely available applications (e.g., email, chat channels) to spread. A worm might attach itself to a piece of outgoing email or use a file transfer command between trusted systems. Worms take advantage of holes in software and exploit systems. Unlike viruses, worms rarely host themselves within a legitimate file or boot area.
In the world of malicious mobile code the phrase "in the wild” means the malicious program is widespread and routinely reported to antivirus researchers. Many rogue programs get created, but never become a big threat to society at large. This can be because they are full of bugs, are too noticeable to spread without quick detection, or remain abstract research programs. A common rogue program might start out in the wild, but end up disappearing because of good antivirus techniques and technology updates. The Pakistani Brain virus was once one of the most popular computer viruses in the world, but it can only infect 360KB floppy diskettes. Once 3.5-inch diskettes took over, the Brain virus had no place to go.
Joe Wells is a
well known figure in the antivirus industry. Since 1993, he has
maintained a monthly list known as the Wild
List
(http://www.wildlist.org). It
records the viruses most frequently reported in the general public.
The viruses on the list are reported by antivirus experts (reporters)
around the world. In order to be on the list, the virus must be
reported by two or more reporters in a given month. Wells’s
list is considered to be among the best virus activity measurement
tools, although it doesn’t measure all types of MMC activity.
So, while a virus scanner may claim to detect over 50,000 different viruses, it’s probably more important that it detects 100 percent of the viruses on the Wild List. The June 2001 list includes 214 different viruses reported by two or more antivirus researchers, with another additional 473 reported without two reporters. Approximately 75 percent of the list is composed of macro viruses, although that statistic is quickly giving away to Internet-based scripting attacks.
How hard can naming a virus be? Very frustrating. Naming rogue code is a semantic Tower of Babel where the only consistency is inconsistency. The nature of malicious mobile code means that it appears in more than one location at the same time and is often received by several different researchers at once. Researchers are more concerned with getting their product to recognize and remove the bug than agreeing on a global name. The first IBM PC virus, Pakistani Brain, is also known as Brain , Nipper , Clone , and Dungeon. One of the latest code attacks, the Happy99 worm, is also known as Ska and I-Worm . It’s almost unusual for a malicious program to only have one name. The most popular title is appointed the official name, while the others become known as aliases. The multiple names make it difficult to discuss viruses when no one is sure who is referring to what.
During the early years, most malicious code was named after a text string found in the code, and that’s still the case with the majority of rogue code today. Occasionally, MMC is named after the location where it was first reported, but this led to many viruses being named after places it did not originate from. For example, the Jerusalem virus originated in Italy, but was first reported at Hebrew University. Some viruses are named after their authors, like the Dark Avenger virus, but this practice is frowned on as it gives undue media attention to the author, which attracts more virus writers. For awhile, researchers considered naming viruses after a random sequence number or after the number of bytes in its code, like Virus 1302. This was an attempt to deny virus authors the legitimacy of even hearing their creation’s name discussed in the press. But it made them hard to remember for researchers and nonresearchers alike.
In 1991, well-respected members of the
Computer Antivirus Researchers
Organization (CARO) came up with a standard naming scheme called the
CARO naming convention. While CARO didn’t
dictate the actual names, it did implement a set of naming rules that
would help antivirus researchers describe viruses. Each virus name
can consist up to five parts:
CARO added other rules, such as:
Don’t name it after a location.
Don’t use company or brand names.
Don’t invent a new name if there is an existing name.
Each designation is a subclass of the other. Thus, the Cascade virus variant, Cunning , which plays music is now designated as Cascade.1701.A. Cascade is the family name, the 1701 group name comes because Cascade comes in a few different sizes (1701, 1704, 1621, etc.), and was the first variant. The Jerusalem Apocalypse variant is called Jerusalem.1808.Apocalypse .
Although the new naming convention helped out a bit, the arrival of so many new ways of infection led most antivirus manufacturers to add another prefix to the beginning of the CARO name to indicate the type of virus. For example, WM means MS-Word macro virus, Win32 means 32-bit Windows viruses, and VBS means Visual Basic Script virus. Thus, one of the Melissa virus variants becomes W97M.Melissa.AA, the Happy99 worm becomes Win32.Happy99.Worm , and the VBScript worm FreeLinks becomes VBS.Freelinks . Of course, it’s still hard to find the same virus with the same name between antivirus manufacturers, but at least the names are more likely to be descriptive.
Table 1-1 shows many of the different prefixes used by antivirus vendors.
Table 1-1. Malicious mobile code prefixes
Thus, the W95.CIH virus name should explicitly tell you that it was written using Windows 95 API calls. And sure enough, the CIH virus can spread on Windows 9x and NT platforms, but its payload will not work under NT. Although each programming language used to write rogue code can result in a different prefix, some malicious code types, like DOS viruses, aren’t routinely assigned a prefix.
VGrep
is an attempt by the antivirus industry to associate all known virus
names in a way that identical viruses can be linked to each
other’s name, regardless of the scanner product. VGrep works by
taking known virus files and scanning them with many different
scanners. The results of the scanners, and the subsequent
identifications, are sent to a database. Each scanner’s results
are compared to the other scanners and used as a virus name
cross-reference. VGrep participants agree
to rename viruses to the most common name, if one can be found. Large
enterprises with tens of thousands of scanners are requiring their
antivirus scanner vendors to use VGrep names, which helps with
tracking multiple code outbreaks in a global environment.
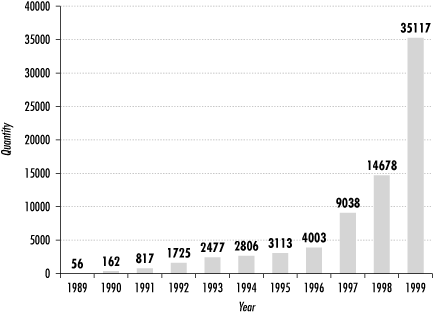
Network Associates, makers of VirusScan™, claims there are over 57,000 different malicious code programs in existence. Although this is the largest number reported by any of the antivirus companies, there are several others detecting 35,000 to 50,000 rogue programs. There have been surveys reporting that over 98 percent of North American businesses have been the victim of rogue code during each year, accounting for an aggregated damage cost of $1 to $3 billion. Trend Micro’s World Virus Tracking Center (http://wtc.trendmicro.com/wtc/) claims over 1,000,000 new infections happen every 24 hours. Figure 1-1 shows the exceptional growth of computer viruses between the early years of PC viruses on into the new century. Numbers are an average taken from many top antivirus vendors.
The International Computer Security
Association Labs (http://www.trusecure.com) reported the
following findings in their
industry-respected
Computer Virus Prevalence
Survey 2000:
The average business surveyed experienced 160 encounters per 1,000 machines per year.
More than half the businesses surveyed experienced a virus disaster (more than 25 computers infected at one time).
Median downtime from a malicious code incident was 21 hours.
More than 80 percent had experienced a virus disaster because of a malicious email.
More than 88 percent of surveyed respondents said they had all the PCs protected with antivirus software.
What is important to note here is that while the majority of networks had antivirus protection, it was not enough. They still experienced malicious mobile code attacks. This book will help you plan steps to maximize your antivirus protection.
Half the households in America now own a personal computer and are connected to the Internet. Most of our schools contain Internet-connected PCs and there are billion-dollar federal initiatives to install new Internet PCs. The number of Internet users in the U.S., ages 16 and up, is near 100 million. Half of all Internet users are female. Young children and grandparents are joining in growing numbers. Like the television and radio, an Internet-connected PC will be a societal norm. With that said, it is estimated that less than 10 percent of home PCs have an antivirus program with update databases. Fewer than that understand the simple, reasonable steps to take to prevent malicious programs from causing harm to their computer systems. This is a fact MMC writers love.
The number of computer users and the amount of MMC programs continue to multiply. The inherent nature of malicious replicating code means that even if no more rogue programs were made, they would continue to harass for years to come. The Stone virus, created in 1988, is still reported as one of the most popular viruses. While viruses continue to be the most popular malicious code written, the threat of remote control Trojans, email attacks, and active content are our biggest risks. The nation’s Internet and computing infrastructure will have to undergo a transformation into a more secure environment, in order for the free exchange of ideas and information to continue. I’ll cover the future of the Internet and malicious mobile code in Chapter 15.
It’s nice to know there are many organizations dedicated to
protecting computer systems against malicious mobile code attacks.
There are commercial vendors,
special interest groups, newsgroups, government agencies, law
enforcement agencies, and consumer-driven organizations, all of which
want to stop viruses, worms, Trojans, and other rogue programs. All
the traditional antivirus companies have recognized the need for
complete coverage against the rising threat of malicious mobile code.
Although they are selling a product, their web sites are some of the
best resources for protection information. You can get free
downloads, free virus- removal software, read white papers, subscribe
to email alert services, and learn prevention tips. There are several
antivirus newsgroups read by knowledgeable consultants waiting to
answer your questions.
alt.comp.virus
is one of the best.
Two of the biggest Internet resources dedicated to protecting your computer against hackers are Pittsburgh’s Carnegie Mellon Computer Emergency Response Team (http://www.cert.org) and the Department of Energy’s Computer Incident Advisory Capability (http://www.ciac.org/ciac). Both sites are interested in total computer security, not just mobile code, and are considered highly reliable resources. You can subscribe to security alert newsletters warning of the latest hacker exploits. While both sites are a great supply of information, they aren’t as current as the commercial vendor web sites. When the latest malicious code outbreak happens, the commercial sites usually have a description and antidote posted within a few hours or a day of the discovery. Although they are improving, CERT and CIAC can be as much as a few weeks behind the curve. Then again, the hype has usually had a chance to die down by then and they are able to give a clearer discussion on the impact of the latest MMC program. Some antivirus vendors have a recurring tendency to overstate the threat of the latest bug in order to sell more software.
Get Malicious Mobile Code now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.