Unless you are seeing specific, recognizable symptoms that can only be a computer virus, always suspect a regular software or hardware issue first. However, here are the steps you should follow if you suspect a machine under your supervision has a Windows virus.
If you suspect a PC is
infected with a computer virus, or any type of malicious mobile code,
the first thing you want to do is unplug the PC from the network
and/or Internet. This will minimize the chances that the PC will be
used to spread the virus beyond its own local drives. Alternatively,
in Windows 2000 you can temporarily disable network connections by
right-clicking My Network Places
, and then choosing
Properties
→
right-click
Local
Area
Connections
→
Disable.
Then you can repeat the process and enable access after the threat is
gone.
An antivirus scanner is an excellent tool to do a preliminary positive identification of the virus. If the antivirus scanner recognizes the virus, follow its directions, and allow it to clean the file(s) or boot area. Today’s Windows scanners are designed to be installed before a virus hits. They start a preliminary scan during bootup by looking at the core files, but the main program is made to be run after Windows has fully loaded.
Tip
Unlike the search for viruses on a DOS computer, Windows virus scanners can be run without booting with a clean, write-protected diskette, if installed ahead of the infection. Still, the best detection rates will be gained if you do scan prior to Windows loading. And most Windows antivirus companies provide boot diskettes for that purpose. Use the boot method if the non-boot method did not find any MMC, but you still have reasons to be suspicious. Unfortunately, many antivirus boot disks cannot access a Windows NT NTFS partition and force the user to boot NT (if possible) before running the antivirus scanning software.
Of course, some computer viruses can hide from scanners if they are loaded into memory before the scanner. If the scanner does not recognize a computer virus infection, but you still have a strong suspicion that a virus exists, follow these steps.
Windows 2000 has a new feature called
AVBOOT
,
or Computer Associates' InoculateIT Antivirus AVBoot
Version 1.1
. It is
a command-line utility created by running
MAKEDISK.BAT from the
\VALUEADD\3RDPARTY\CA_ANTIV folder. Running
MAKEDISK.BAT
creates a bootable floppy diskette that will search memory and scan
all local hard drives looking for MBR and boot sector viruses. Like
any antivirus scanner, you must keep the signature up to date in
order for it to be effective. The boot diskette includes instructions
on how to update the virus signature database.
The most important thing to note with a PC having bootup problems is where the problem occurs in the boot process. Earlier, we described the different boot sequences for the different Windows platforms. If the problem or error message occurs before the Windows executable or kernel begins to load, that means the problem is related to the BIOS, hard drive boot sector, or partition table. If Windows begins to load, but then bombs quickly, the problem is with the boot sector, a kernel executable, or device driver. Lastly, if the problem occurs after Windows has booted up, but just before or after you are able to log on, you should suspect a corruption problem with one of the programs Windows automatically starts up.
For instance, if you restart a Windows NT PC and the system freezes immediately on a blank, black screen, then one of the following is corrupted: BIOS, MBR, boot record, partition table, or NTLDR. If Windows NT gets to the blue screen text mode, and begins to have problems, suspect a bad or corrupted device driver. If an NT PC gets loaded to the logon screen or desktop and then freezes, suspect a startup service or application.
If your PC won’t even boot into Windows, troubleshoot the boot problem as if were not a virus-related problem (although it cannot hurt if you run a boot diskette virus scan against the hard drive at this point). Try using a boot disk and seeing if you can get to the hard drive. If you can get to the hard drive with a boot disk, it means the hard drive might have a corrupted boot sector or partition table. Run the normal recovery processes to fix those problems (most of the hard disk boot sector recovery techniques introduced in Chapter 2 should work for Windows 3.x and 9x). If any version of Windows indicates that it has a problem with 32-bit disk access, suspect a boot sector virus.
If Windows NT has a boot problem, it will usually tell you what file in the boot process is corrupted or missing, or give you a blue screen error. Record the first few lines of information on the blue screen and research the specific error message on Microsoft’s Internet Knowledge Base (http://support.microsoft.com/directory/). Windows 2000’s STOP errors are getting easier to read than their counterparts with lots of plain text and advice.
Running
SCANDISK.EXE
will check the computer for physical and logical hard drive problems.
Whether or not SCANDISK finds an error
doesn’t rule out a virus infection. However, if the problem is
simply a disk corruption problem without a virus involved, the
subsequent fix can minimize the problem. If prompted to fix a
problem, always create an undo disk. The
CHKDSK.EXE
command line program can perform some limited disk analysis to scan
and repair hard drive problems in Windows 3.x, NT, and 2000. It works
on both FAT and NTFS volumes in NT and 2000. Run
CHKDSK with the /?
parameter to get a list of all available parameters.
CHKDSK /F is the same process Windows NT and
2000 goes through during every bootup to determine that the disk
logical partitions are functional. The CHKDSK /F
routine, on FAT volumes, will analyze the FAT tables and replace them
with the FAT copy if corruption is detected.
Windows 9x will not allow CHKDSK to check the
hard drive or fix disk problems. Windows NT will not allow
CHKDSK to run while the disk volumes are in use,
but will schedule a CHKDSK run at the next
startup. Windows 2000’s CHKDSK will allow
you to dismount the volume, causing all open files not to be saved,
and then run (without rebooting).
Warning
In some rare cases, running SCANDISK can cause
even more damage to a computer hard drive if particular viruses are
involved. That is why you should always run a quick virus scan first,
as it always looks for these types of viruses and will tell you if
they are in memory. The risk from viruses of this type is low, as
they are not widespread.
If you have Windows 9x or Windows 2000,
boot to Safe mode to minimize the number of programs and processes in
memory. Safe mode can be accessed by choosing F8
during the Windows boot process. Among other things, Safe mode
bypasses programs loaded from the run areas of the registry; a place
where viruses and Trojans love to load. Unfortunately, neither
Windows 3.x or earlier versions of NT have this functionality.
Search for EXE and
DLL files with new file creation or modification
dates. On Windows 9x and NT, use
Start
→
Find
→
Files
or
Folders, in Windows ME or
2000 it is
Start
→
Search
→
For Files or Folders. I tell Windows to look for all
*.EXE or *.DLL files and I
use the Date tab to narrow the files found to
those modified recently.
If you have Windows ME, look at xFP’s history log file,
SPLOG.TXT
,
to see if there is a recent history of protected system files that
were modified or deleted. Windows 2000 records xFP activities in the
System log.
While xFP may have protected particular files, a large number of
unsuccessful attempts may mean a virus has been successful with
nonprotected files. In Windows NT or 2000, you might consider
auditing file object accesses. In User
Manager (for Domains), choose
Policies
→
Audit
→
Audit
These
Events and enable
Success and Failure for
File and Object Access. All file and object
accesses will begin being tracked and reported in the
Security log of the Event
Viewer. This is not my favorite troubleshooting tool,
because what you’ll see in the log is tough to understand even
when you’re an expert (it reads a bit better in Windows 2000).
It takes awhile to get accustomed to Microsoft’s security
auditing, but if you study the detail enough, you will get a sense if
an unknown program is modifying your system.
It is not unusual to see recently modified EXE
or DLL files, even on a clean system, if new
programs or downloads have been installed. And different Windows
programs, unfortunately, store and update information within their
own programming files. You should look for blatant signs of virus
modification, such as many modified EXE files
within the same folder, or dozens of newly modified program files
located in different directories, but all modified on the same date.
And, of course, your core Windows executables such as
KERNEL32.DLL
and
GDI.EXE
should not be newly modified.
If I find newly modified EXE files that are not
being detected by the scanner as infected, I might run a few of them
to get them in memory (if they will start). Then, I will start other
programs without newly modified dates as bait, use them, close them,
and then look to see if even more modified files turn up. If you find
more files with new modification dates, you can quickly assume that
you have a virus.
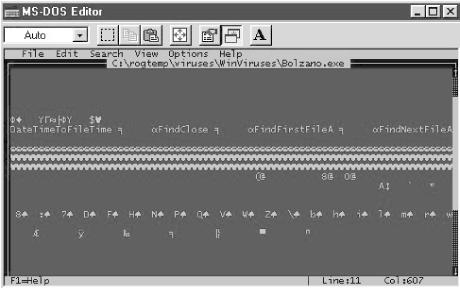
If you find any suspicious newly modified files, you should open them with an ACSII editor and take a quick look. Although viruses are frequently encrypted, often virus writers leave clues within the coding that are clearly visible as text. Seeing dubious words and phrases (such as FileFind, FileDelete, *.EXE, Gotcha, Virus Lab 1.1,or Kill) should be a quick indication that the file is malicious. Figure 4-1 shows the contents of a file infected by Win32.Bolzano.
You can see text references to finding files and a command used to
save the file’s modification time and date. The file also
contains references to NTLDR and
NTOSKRNL.EXE
(not shown), both of which have little reason to be named in a
legitimate file. Also, early on in the file there are text references
to .EXE and .SCR files,
deleting files, creating files, and the name Bolzano. Even if I
didn’t know the file was a virus, I would be somewhat
suspicious now. It is not unusual to find some legitimate files that
search for particular types of files, as they can appear in any
program that needs to create and manipulate files. But if I see
enough text to indicate that a suspicious executable is looking for
or deleting files, I’ll look for other text strings that would
not be present. For example, when examining a client’s PC and
finding suspicious executables, I saw the same sorts of text strings
that are displayed in Figure 4-1. I began looking
even closer at the files and found a text string that said
V5I%R#U@3S!!. Maybe it was just luck, but I was
able to pick up the word VIRUS embedded in the
string, and then I knew that, the file was infected with a newly
encrypted version of the Win95.Marburg virus.
Using SYSEDIT,
REGEDIT, MSCONFIG, MSINFO32
or
DRWATSON
, look for untrusted programs in the
startup regions of the boot process. This means checking
AUTOEXEC.BAT, CONFIG.SYS, WINSTART.BAT, DOSSTART.BAT,
Startup Group, Registry,
Win.INI
,
and
SYSTEM.INI
for autostarting programs.
MSINFO32.EXE
is a great troubleshooting utility. Not only will it list all the
hooked interrupts, drives, devices, and programs loaded, but it
displays all startup programs (Software Environment
→
Startup Programs).
MSINFO32 gives you a wealth of information about
your system. Of course, this means you have to be familiar with what
your machine is normally running in the first place. The
Tools menu option in MSINFO32
is full of shortcuts to other troubleshooting utilities, like
Version Conflict
Manager
, Registry
Checker
, Signature Verification
Tool
, System File
Checker
, Dr. Watson, and
Scandisk. The use of Dr. Watson is covered in
more detail in Chapter 6.
In the Windows 9x environment, computer
viruses often load as VxD drivers. You can start Windows 9x and press
F8 during the startup and choose to create a
BOOTLOG.TXT
file. This file can be examined after Windows has booted and reveal
something similar to Example 4-1. It contains a list
of the device drivers and processes, and whether they were successful
or failed.
Example 4-1. Example portion of a BOOTLOG.TXT file
[0007FF34] Loading Device = C:\WinDOWS\HIMEM.SYS (Logo disabled) [0007FF37] LoadSuccess = C:\WinDOWS\HIMEM.SYS [0007FF48] Loading Device = C:\WinDOWS\DBLBUFF.SYS [0007FF4A] LoadSuccess = C:\WinDOWS\DBLBUFF.SYS [0007FF57] Loading Device = C:\WinDOWS\IFSHLP.SYS [0007FF58] LoadSuccess = C:\WinDOWS\IFSHLP.SYS [0007FF82] C:\PROGRA~1\NORTON~1\NAVDX.EXE[0007FF82] starting [00080170] Loading Vxd = VMM [00080170] LoadSuccess = VMM [00080170] Loading Vxd = C:\WinDOWS\SMARTDRV.EXE [00080172] LoadSuccess = C:\WinDOWS\SMARTDRV.EXE [000801A2] Loading Vxd = vnetsup.vxd [000801A2] LoadSuccess = vnetsup.vxd [000801A7] Loading Vxd = ndis.vxd [000801A9] LoadSuccess = ndis.vxd [000801AA] Loading Vxd = ndis2sup.vxd [000801AA] LoadFailed = ndis2sup.vxd [000801AE] Loading Vxd = JAVASUP.VXD [000801AF] LoadSuccess = JAVASUP.VXD [000801AF] Loading Vxd = CONFIGMG [000801AF] LoadSuccess = CONFIGMG [000801AF] Loading Vxd = NTKERN [000801AF] LoadSuccess = NTKERN
Although the file will list hundreds of names, look for ones that
were listed with new modification dates from Step 6, or for the ones
that failed to load. Do a quick search for the word
Fail to locate all instances of failure. Do
research on the Internet for new VxDs or ones that have failed. If
you can’t identify it, temporarily rename it, and reboot. See
if the suspicious behavior goes away.
Viruses can load in Windows NT as SYS drivers. You can start Windows
NT in a special diagnostic mode that shows the different device
drivers loading. To do so, edit the BOOT.INI to
add the /SOS switch at the end of the line which
starts
NTOSKRNL.EXE
.
In Windows 98, choose F8 while it boots and choose
Single Step mode. You can see the individual kernel and device
drivers as they load (or don’t load). Although you don’t
necessarily have to memorize what are the correct drivers to be
loading at boot time (in fact it is nearly impossible), you should
keep an eye out for strange-sounding names or names that are
misspelled by one letter (a common virus trick).
As we discussed before,
many computer viruses inadvertently disable the 32-bit disk and
memory management processes in Windows. In Windows 9x, choose
Start
→
Settings
→
Control
Panel
→
System
→
Performance.
Note any performance degradations and suspect virus activity for any
downgrades.
Certainly, if you receive unexpected notification messages from Windows ME’s System File Protection or Windows 2000’s Windows File Protection, consider the possibility of malicious mobile code. Especially, if it happens after running an unexpected executable sent to you in email.
At this point, if you don’t see anything suspicious, consider treating the problem as a nonmalicious code event. You can, of course, call a malicious code expert to verify or send suspect files to an antivirus company via the Internet. They will usually look at individual files for free and let you know if it contains malicious mobile code.
Get Malicious Mobile Code now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.