Trojan and Worm Examples
In this section of the chapter, I will cover a wide range of example Trojans and worms. I will spend more time on the first Trojan, Back Orifice, because it is representative of the largest Trojan threats.
Back Orifice
Back Orifice 2000, or BO2K, as it is known, was released in July 1999 under the public GPL GNU license. It is free for anyone to use or modify. It is very configurable, with point and click GUI configuration screens. The Back Orifice Trojan, like most RATs, has two parts: a server and a client. The server portion is preconfigured by the hacker and then somehow placed on the victim’s machine. When the server program is executed, it automatically installs itself, hides its presence, and opens a new port number on the host machine. Often, if the right plug-in is included, it will email the hacker with the IP address of the new host victim. The client program is used by hackers to locate and manipulate server programs. The client and server programs must match many configuration parameters in order to find each other. A client using the common port number of 31337 over TCP with XOR encryption will not work with a server using the UDP protocol or CAST-256 encryption. As shown in Figure 6-2, Back Orifice has a user-friendly GUI to help configure the server executable that will be placed on the victim’s PC.
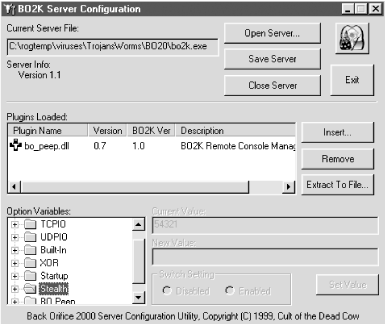
Figure 6-2. Back Orifice’s server configuration ...
Get Malicious Mobile Code now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

