Back-to-Back Firewalls
The ideal approach to any perimeter network or DMZ is to utilize two different security devices such that one provides a layer of defense from the Internet to the perimeter network and the other provides another layer of defense by filtering traffic between the perimeter network and the internal network. The Lync Server Edge Servers are situated between the two firewalls in the perimeter network. This approach is illustrated in Figure 31.3.
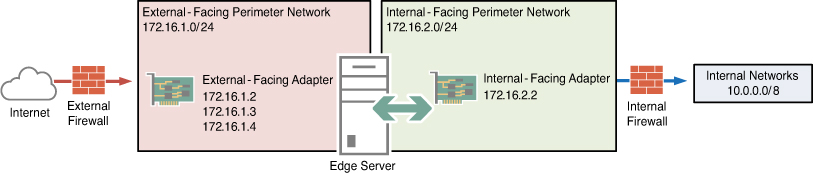
Figure 31.3. Back-to-back firewalls.
This configuration is generally considered the most secure because even if an attack compromises the external firewall, the internal firewall still ...
Get Microsoft® Lync® Server 2013 Unleashed Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

