Chapter 1. Network Security Assessment
This chapter discusses at a high level the rationale behind Internet-based network security assessment and penetration testing. To retain complete control over your networks and data, you must take a proactive approach to security, an approach that starts with assessment to identify and categorize your risks. Network security assessment is an integral part of any security life cycle.
The Business Benefits
From a commercial standpoint, assurance of network security is a business enabler. As a security consultant at the time of writing, I am helping a particular client in the retail sector to deploy and secure an 802.11b wireless network for use in nearly 200 stores across the United Kingdom. This wireless network has been designed in a security-conscious manner, allowing the retailer to embrace wireless technologies to improve efficiency and the quality of their service.
Shortcomings in network security and user adherence to security policy often allow Internet-based attackers to locate and compromise networks. High-profile examples of companies who have fallen victim to such determined Internet-based attackers over the last four years include:
RSA Security (http://www.2600.com/hacked_pages/2000/02/www.rsa.com/)
OpenBSD (http://lists.jammed.com/incidents/2002/08/0000.html)
NASDAQ (http://www.wired.com/news/politics/0,1283,21762,00.html)
Playboy Enterprises (http://www.vnunet.com/News/1127004)
Cryptologic (http://lists.jammed.com/ISN/2001/09/0042.html)
These compromises have come about in similar ways, involving large losses in some cases. Cryptologic is an online casino gaming provider that lost $1.9 million in a matter of hours to determined attackers. In the majority of high profile incidents, the attackers used a selection of the following techniques:
Compromising a poorly configured or protected peripheral system that is related to the target network space or host using publicly available exploits, such as scripts available from Packet Storm (http://www.packetstormsecurity.org) and other archives
Directly compromising key network components using private exploit tools, such as scripts that the attacker or his hacking group have developed for their own personal use
Compromising traffic and circumventing security mechanisms using ARP redirection and network sniffing
Compromising user account passwords and using those passwords to compromise other hosts where the user may have an active account
Abusing blatant system or network configuration issues, reading sensitive information from publicly accessible web folders, or bypassing poor firewall rules that open up the network to attack
To protect networks and data from determined attack, you need assurance and understanding of the technical security of the network, along with adherence to security policy and incident response procedures. In this book, I discuss assessment of technical security and improving the integrity and resilience of IP networks. Taking heed of the advice presented here and acting in a proactive fashion ensures a decent level of network security.
IP: The Foundation of the Internet
The Internet Protocol Version 4 (IPv4) is the networking protocol suite all public Internet sites currently use to communicate and transmit data to one another. From a network security assessment methodology standpoint, this book comprehensively discusses the steps that should be taken during the security assessment of any IPv4 network.
Tip
IPv6 is an improved protocol that is gaining popularity among academic networks. IPv6 offers a 128-bit network space (3.4 x 1038 addresses) as opposed to the 32-bit space of IPv4 (only 4 billion addresses) that allows a massive number of devices to have publicly routable addresses. Eventually, the entire Internet will migrate across to IPv6, and every electronic device in your home will have an address.
Due to the large size of the Internet and sheer number of security issues and vulnerabilities publicized, opportunistic attackers (commonly referred to as script kiddies ) will continue to scour the public IP address space seeking vulnerable hosts. The combination of new vulnerabilities being disclosed on a daily basis, along with the adoption of IPv6, ensures that opportunistic attackers will always be able to compromise a certain percentage of Internet networks.
Classifying Internet-Based Attackers
The first type of threat that all publicly accessible networks are at risk from is that posed by opportunistic attackers. These attackers use auto-rooting scripts and network scanning tools to find and compromise vulnerable Internet hosts. Most opportunistic attackers fall into two distinct groups:
The second type of threat is that posed by determined attackers. A determined attacker will exhaustively probe every point of entry into a target network from the Internet, port scanning each and every IP address and assessing each and every network service in depth. Even if the determined attacker can’t compromise the target network on his first attempt, he will be aware of areas of weakness. Detailed knowledge of a site’s operating systems and network services allows the determined attacker to compromise the network upon the release of new exploit scripts in the future.
In light of this, the networks that are most at risk are those with sizeable numbers of publicly accessible hosts. Having many entry points into a network multiplies the exploitable vulnerabilities that exist at different levels; managing these risks becomes an increasingly difficult task as networks grow.
Assessment Service Definitions
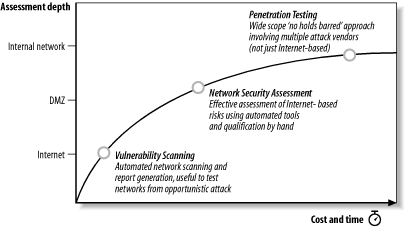
Most security providers (both service and product companies) offer a number of assessment services branded in a variety of ways. Figure 1-1 shows the key service offerings along with the depth of assessment and relative cost. Each service type can provide varying degrees of security assurance.
Vulnerability scanning uses automated systems (such as ISS Internet Scanner, QualysGuard, or eEye Retina) with minimal hands-on qualification and assessment of vulnerabilities. This is an inexpensive way to ensure that no obvious vulnerabilities exist, but it doesn’t provide a clear strategy to improve security.
Network security assessment lies neatly between vulnerability assessment and full-blown penetration testing; it offers an effective blend of tools and hands-on vulnerability testing and qualification by trained analysts. The report is usually hand-written, giving professional advice that can improve a company’s security.
Full-blown penetration testing is outside the scope of this book; it involves multiple attack vectors (e.g., telephone war dialing, social engineering, wireless testing, etc.) to compromise the target environment. Instead this book fully demonstrates and discusses the methodologies adopted by determined Internet-based attackers to compromise IP networks remotely, which in turn will allow you to improve IP network security.
Network Security Assessment Methodology
The best practice assessment methodology used by determined attackers and network security consultants involves four distinct high-level components:
This complete methodology is relevant to Internet-based networks being tested in a blind fashion with limited target information (such as a single DNS domain name). If a consultant is enlisted to assess a specific block of IP space, he skips initial network enumeration and commences bulk network scanning and investigation of vulnerabilities.
Internet Host and Network Enumeration
Publicly available reconnaissance techniques, including web and newsgroup searches, Network Information Center (NIC) WHOIS querying, and Domain Name System (DNS) probing, are used to collect data about the structure of the target network from the Internet without actually scanning the network or necessarily probing it directly.
Initial reconnaissance is very important because it identifies hosts that aren’t properly fortified from attack. A determined attacker invests time in identifying peripheral networks and hosts, while companies and organizations concentrate their efforts on securing obvious public systems (such as public web and mail servers) but neglecting hosts and networks that lay off the beaten track.
It may well be the case that a determined attacker also enumerates networks of third party suppliers and business partners that, in turn, have access to the target network space. Nowadays such third parties often have dedicated links into areas of internal corporate network space through VPN tunnels and other links.
Key pieces of information that are gathered through initial reconnaissance include details of Internet-based network blocks, internal IP addresses gathered from DNS servers, insight into the target organization’s DNS structure (including domain names, subdomains, and hostnames), and IP network relationships between physical locations.
This information is then used to perform structured bulk network scanning and probing exercises to assess further the target network space and investigate potential vulnerabilities. Further reconnaissance involves extracting user details (including email addresses), telephone numbers, and office addresses.
Bulk Network Scanning and Probing
After identifying public IP network blocks that are related to the target network space, analysts should carry out bulk TCP, UDP, and ICMP network scanning and probing to identify active hosts and accessible network services (e.g., HTTP, FTP, SMTP, POP3, etc.), that can in turn be abused to gain access to trusted network space.
Key pieces of information that are gathered through bulk network scanning include details of accessible hosts and their TCP and UDP network services, along with peripheral information such as details of ICMP messages to which target hosts respond, and insight into firewall or host-based filtering policies.
After gaining insight into accessible hosts and network services, analysts can begin offline analysis of the bulk results and investigate the latest vulnerabilities in accessible network services.
Investigation of Vulnerabilities
New vulnerabilities in network services are disclosed daily to the security community and underground alike, through Internet mailing lists and public forums including Internet Relay Chat (IRC). Proof-of-concept tools are often published for use by security consultants, whereas full-blown exploits are increasingly retained by hackers and not publicly disclosed in this fashion.
Here are five web sites that are extremely useful for investigating potential vulnerabilities within network services:
SecurityFocus (http://www.securityfocus.com)
Packet Storm (http://www.packetstormsecurity.org)
CERT vulnerability notes (http://www.kb.cert.org/vuls/)
MITRE Corporation CVE (http://cve.mitre.org)
ISS X-Force (http://xforce.iss.net)
SecurityFocus hosts many useful mailing lists including BugTraq , Vuln-Dev, and Pen-Test . These can be subscribed to by email, and archived posts can be browsed through the web site. Due to the sheer number of posts through these lists, I personally browse the mailing-list archives only every couple of days.
Packet Storm actively archives underground exploit scripts, code, and other files. If you are in search of the latest public tools to compromise vulnerable services, Packet Storm is a good place to start. Often, SecurityFocus provides only proof-of-concept or old exploit scripts that aren’t effective in some cases.
Lately, Packet Storm has not been updated as much as it could be, so I increasingly browse databases such as the MITRE Corporation Common Vulnerabilities and Exposures (CVE), ISS X-Force, and CERT vulnerability notes lists. These lists allow for effective collation and research of all publicly known vulnerabilities so that exploit scripts can be located or built from scratch.
Investigation at this stage may also mean further qualification of vulnerabilities. Often it is the case that bulk network scanning doesn’t give detailed insight into service configuration and certain enabled options, so a degree of manual testing against key hosts is often carried out within this investigation phase.
Key pieces of information that are gathered through investigation include technical details of potential vulnerabilities along with tools and scripts to qualify and exploit the vulnerabilities present.
Exploitation of Vulnerabilities
Upon qualifying potential vulnerabilities in accessible network services to a degree that it’s probable that exploit scripts and tools will work correctly, attacking and exploiting the host is the next step. There’s not really a lot to say about exploitation at a high level, except that by exploiting a vulnerability in a network service and gaining unauthorized access to a host, an attacker breaks computer misuse laws in most countries (including the United Kingdom, United States, and many others). Depending on the goal of the attacker, she can pursue many different routes through internal networks, although after compromising a host, she usually undertakes the following:
Gain superuser privileges on the host
Download and crack encrypted user-password hashes (the SAM database under Windows and the /etc/shadow file under most Unix-based environments)
Modify logs and install a suitable backdoor to retain access to the host
Compromise sensitive data (databases and network-mapped NFS or NetBIOS shares)
Upload and use tools (network scanners, sniffers, and exploit scripts) to compromise other networked hosts
This book covers a number of specific vulnerabilities in detail but leaves cracking and pilfering techniques (deleting logs, installing back doors, sniffers and other tools) to the countless number of hacking books available. By providing you with technical information related to network and application vulnerabilities, you will be able to formulate effective countermeasures and risk-mitigation strategies.
The Cyclic Assessment Approach
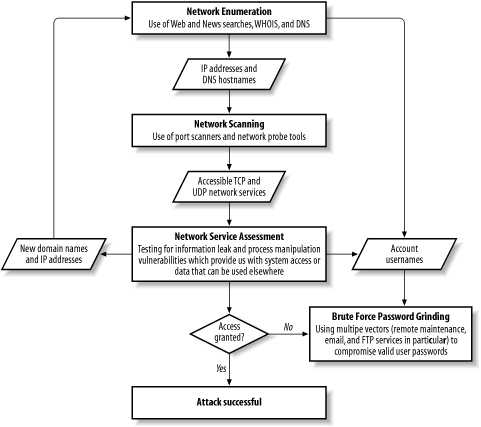
Assessment of large networks in particular can become a very cyclic process if you are testing the networks of an organization in a blind sense and are given minimal information. As you test the network, information leak bugs can be abused to find different types of useful information (including trusted domain names, IP address blocks, and user account details) that is then fed back into other processes. Figure 1-2s flowchart defines this approach and the data being passed between processes.
This flowchart starts with network enumeration, then bulk network scanning, and finally specific service assessment. It may be the case that by assessing a rogue non-authoritative DNS service an analyst may identify previously unknown IP address blocks, which can be fed back into the network enumeration process to identify further network components. In the same way, an analyst may enumerate a number of account usernames by exploiting public folder information leak vulnerabilities in Microsoft Outlook Web Access, which can be fed into a brute-force password grinding process later on.
Get Network Security Assessment now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.