Chapter 10. Assessing VPN Services
VPN services provide access to remote users and branch offices through IPsec, PPTP, and TLS. Service endpoints can be abused to obtain sensitive data, gain network access, and impact availability through denial of service. This chapter focuses on IPsec and PPTP protocols. TLS is increasingly used to provide secure network access, as described in Chapter 11.
IPsec
IP is an inherently unsafe protocol, lacking confidentiality, integrity, and authentication. When implemented correctly, IPsec negates the following attack classes:
-
Network sniffing
-
Source forgery (IP spoofing)
-
Modification of data within packets
-
Replay attacks
Internet Key Exchange (IKE)1 is used to authenticate IPsec peers and set VPN parameters. A security association (SA) is established, defining the IPsec protocols used when sending material, plus cryptographic algorithms, keys, and their expiry (known also as lifetime). The process is summarized in Figure 10-1.
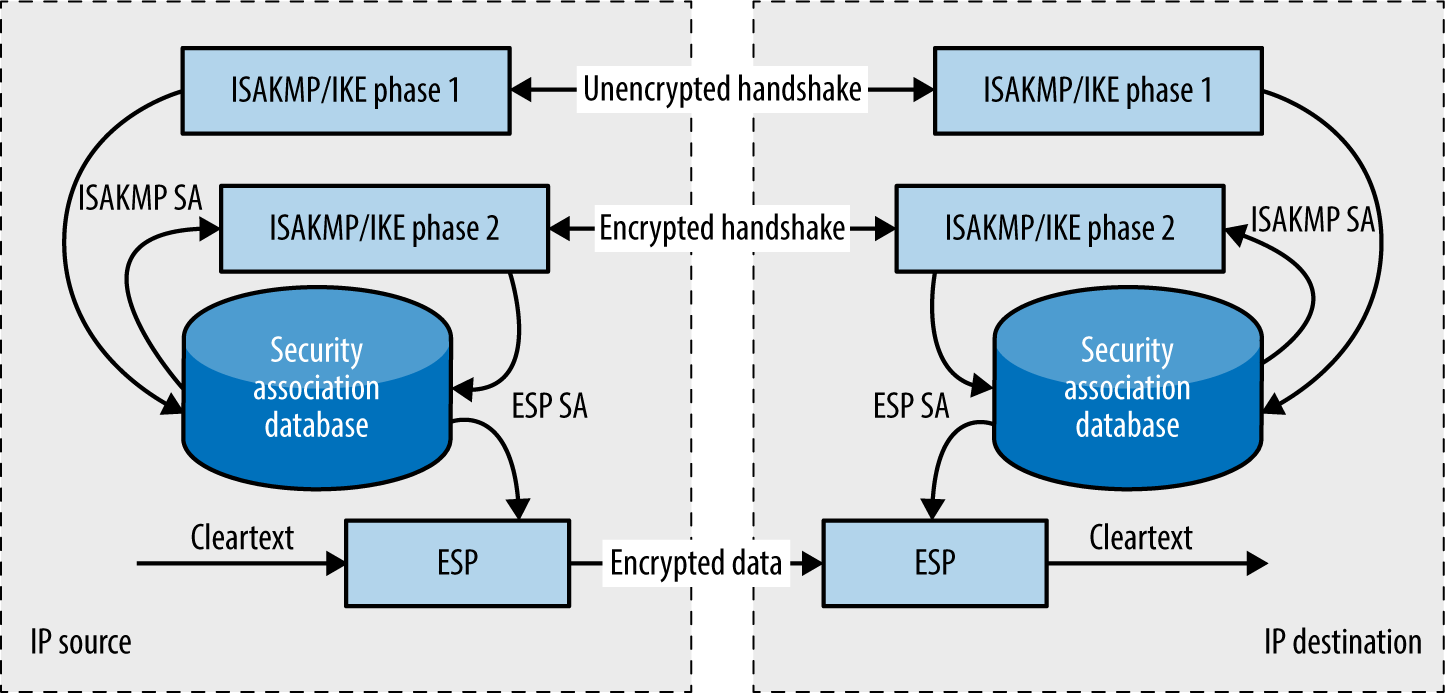
Figure 10-1. Setup and use of an IPsec tunnel with IKE
Packet Format
Mutually agreed IPsec SA fields define the security features used between peers. Figure 10-2 shows an example IP datagram using IPsec in tunnel mode. The Authentication Header (AH)2 provides integrity and data origin authentication with an HMAC of the IP datagram. The Encapsulating Security Payload (ESP)3 encapsulates and encrypts IP datagrams, ...
Get Network Security Assessment, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

