Chapter 13. Assessing Web Servers
Web servers demand a high degree of assurance because they are often exposed to untrusted networks. I discuss tactics and tools used to test these servers and their enabled subsystems in this chapter. Assessment of application frameworks (e.g., Microsoft ASP.NET and Rails) is covered in Chapter 14.
Assessment and hardening of web servers, frameworks, and applications fill entire books. Here I present a concise methodology for fingerprinting, investigating, and qualifying vulnerabilities within available HTTP services, involving the following steps:
-
Identification of proxy mechanisms
-
Enumeration of virtual hosts and accessible websites
-
For each site identified:
-
Profiling the server software and available subsystems
-
Active scanning and crawling to identify useful content and functionality
-
Attacking exposed authentication mechanisms
-
Qualifying vulnerabilities in server software
-
Web applications are often presented through load balancers, and so the first two steps are important. Consider Figure 13-1, in which a client connection is made over TLS to a load balancer that is then directed to an application server internally (via HTTP) based on the Host value provided.
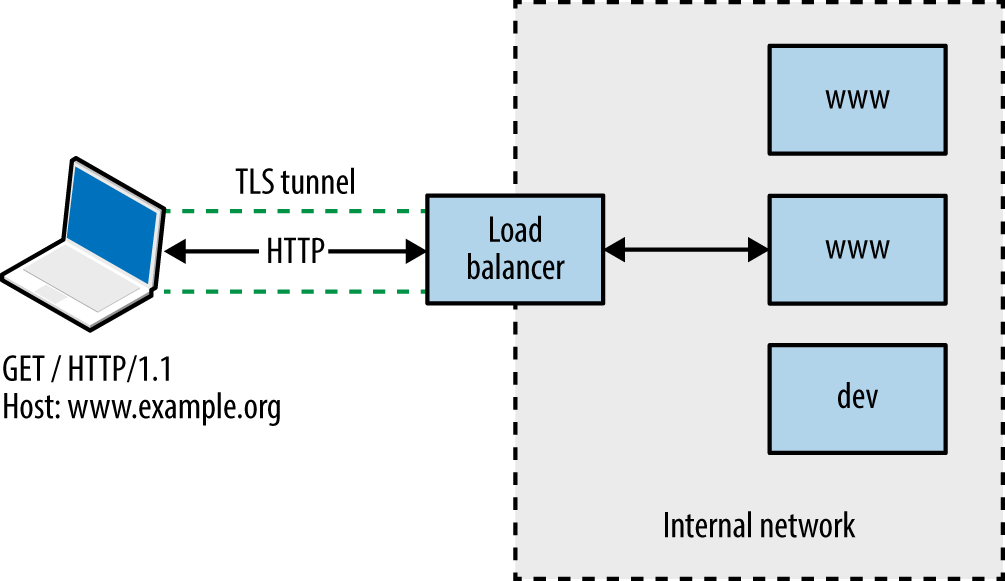
Figure 13-1. Connecting to a virtual host via HTTP 1.1 and TLS
You will encounter one of three scenarios during testing:
-
Directly accessing a single server hosting ...
Get Network Security Assessment, 3rd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

